Cloud computing security is an essential aspect that is gaining immense importance in today's digital world. As technology advances at a rapid pace, the need to protect sensitive data, applications, and infrastructure hosted on the cloud becomes paramount. In this post, we will delve into the nuances of cloud computing security architecture and explore its various components.
Cloud Computing Security Architecture - Ensuring Data Protection
One of the primary objectives of cloud computing security architecture is to ensure the confidentiality, integrity, and availability of data stored on the cloud. By employing robust security measures, organizations can safeguard their sensitive information from potential threats, unauthorized access, and data breaches.
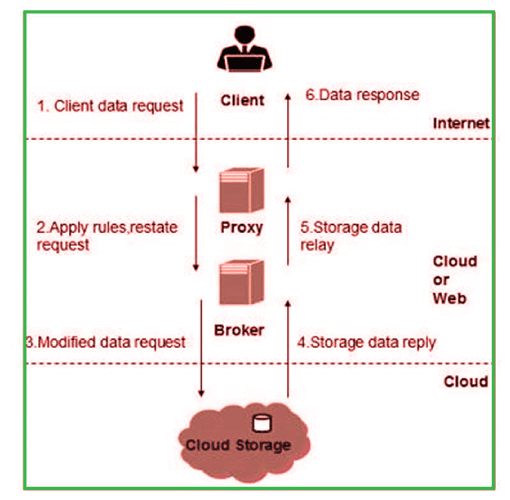
Cloud computing security architecture encompasses several key elements, each playing a crucial role in the overall security framework. Let's explore some of these components:
1. Identity and Access Management (IAM)

IAM ensures that only authorized individuals have access to the cloud resources. It involves authentication mechanisms, access control policies, and user management. By implementing strong authentication protocols like multifactor authentication and robust access control mechanisms, organizations can effectively protect their resources from unauthorized usage.
2. Data Encryption
Data encryption plays a crucial role in protecting the confidentiality of sensitive information. It involves converting the data into an unreadable format that can only be deciphered with an encryption key. By employing strong encryption algorithms, organizations can prevent unauthorized parties from accessing and understanding the data, even if it gets intercepted during transmission or storage.
3. Network Security
Network security within the cloud computing security architecture focuses on securing the communication channels and preventing unauthorized access. It involves implementing firewalls, intrusion detection systems, and virtual private networks (VPNs). These measures ensure that the network remains protected from external threats and that data transmission remains secure.
4. Cloud Provider Security
Choosing a reliable and trustworthy cloud service provider is essential for ensuring robust cloud computing security architecture. Organizations should thoroughly assess the security measures implemented by the provider, including physical security, personnel security, incident response plans, and data backup policies. It is imperative to partner with a provider that aligns with your organization's security requirements.
5. Security Monitoring and Incident Response
Continuous monitoring of cloud infrastructure is crucial to identify any potential security incidents or breaches. This involves implementing security information and event management (SIEM) systems, intrusion detection systems, and performing regular security audits. Furthermore, organizations should establish an incident response plan to ensure a prompt and effective response to any security incidents, minimizing any potential damage.
In conclusion, cloud computing security architecture plays a pivotal role in protecting sensitive data and resources hosted on the cloud. By implementing robust security measures, organizations can mitigate the risks associated with cloud computing and ensure the confidentiality, integrity, and availability of their data. Remember, investing in a comprehensive cloud computing security architecture is not an option; it is a necessity in today's digital landscape.
If you are searching about Cloud Computing Security Architecture Slideshare / Architecture Of you've came to the right place. We have 35 Pics about Cloud Computing Security Architecture Slideshare / Architecture Of like Cloud Computing Security Architecture [12] | Download Scientific Diagram, Cloud Computing Security Architecture for IaaS, SaaS, and PaaS and also 08_02_Pattern_011_15_Cloud_Computing.png (780×950) | Security. Read more:
Cloud Computing Security Architecture Slideshare / Architecture Of
 veggieboxadventures.blogspot.com
veggieboxadventures.blogspot.com computing
101 Guide On Cloud Security Architecture For Enterprises | CSA
Security Architecture Review Of A Cloud Native Environment | Claranet
 www.claranetcybersecurity.com
www.claranetcybersecurity.com entities workflow
Cloud Computing Challenges And Related Security Issues. A Survey Paper
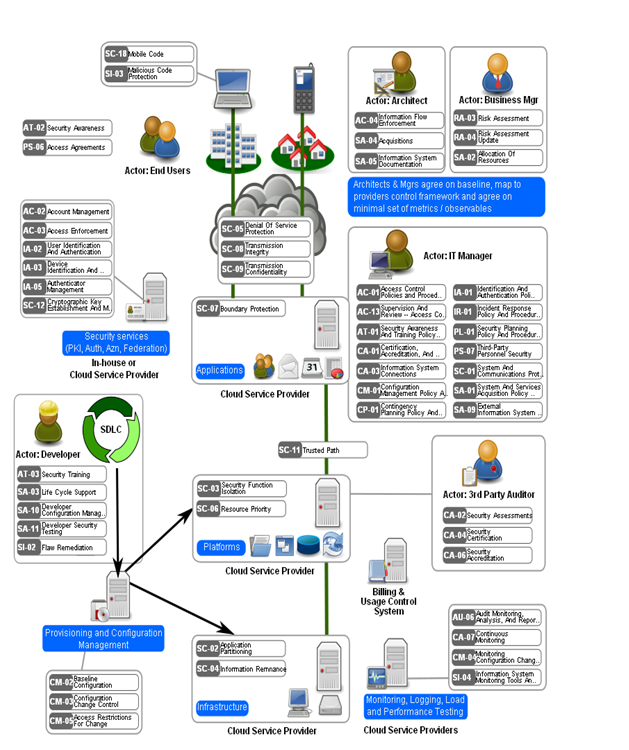 www.cse.wustl.edu
www.cse.wustl.edu cloud computing architecture secure security model open models issues challenges figure
(PDF) Data Security And Privacy Protection Issues In Cloud Computing
 www.researchgate.net
www.researchgate.net Common Roles In Cloud Computing – BMC Software | Blogs
 www.bmc.com
www.bmc.com computing nist roles modello roadmap ceh fututro concettuale coders kurzweilai
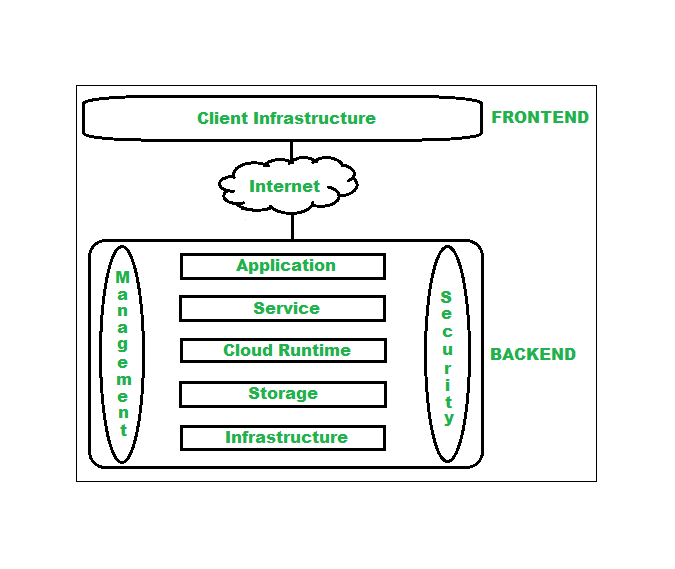
Backend Computing - Backends For Frontends Pattern Cloud Design
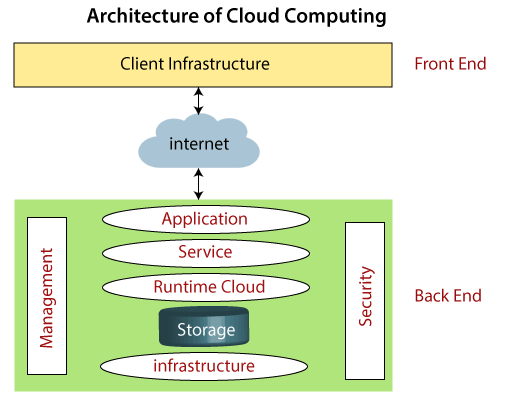 dfsso.blogspot.com
dfsso.blogspot.com javatpoint backend backends frontends denote runtime
Cloud Computing Security Architecture For IaaS, SaaS, And PaaS
 www.sdxcentral.com
www.sdxcentral.com Best Practices For Data Security In Cloud Computing | TurningCloud
 www.turningcloud.com
www.turningcloud.com maturing component rapidly enterprise
Introduction To Cloud Security Architecture From A Cloud Consumer's
/filters:no_upscale()/articles/cloud-security-architecture-intro/en/resources/fig 3.jpg) www.infoq.com
www.infoq.com Tutorial:Cloud Computing Security | Digital Marketing Agency | Web
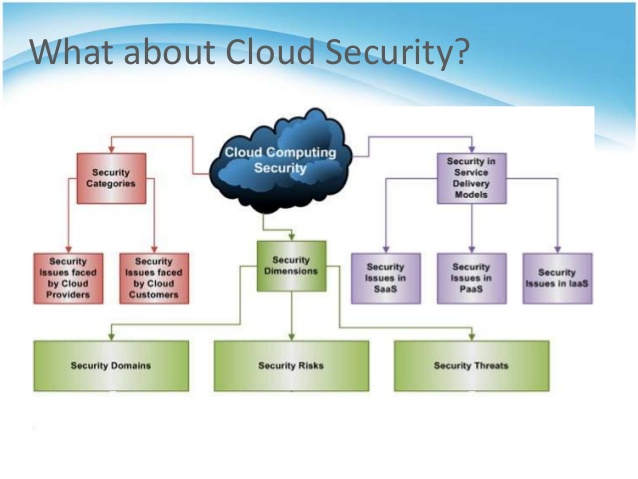 websitetoon.com
websitetoon.com Cloud Computing Security Architecture - Javatpoint
 www.javatpoint.com
www.javatpoint.com Data Center, Cloud Computing Security, And Storage Solutions | CTSBoston
 ctsboston.com
ctsboston.com security cloud computing data center
Cloud Computing Security Architecture | Download Scientific Diagram
Cloud Architecture Layers And Related Security Issues | Download
 www.researchgate.net
www.researchgate.net Why Is Cloud Computing Security Crucial For Your Business - SuperAdmins
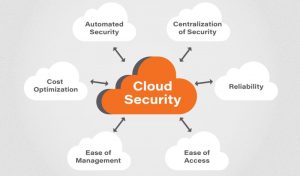 superadmins.com
superadmins.com computing crucial benefits
Cloud Computing - 初识4 Cyber Security
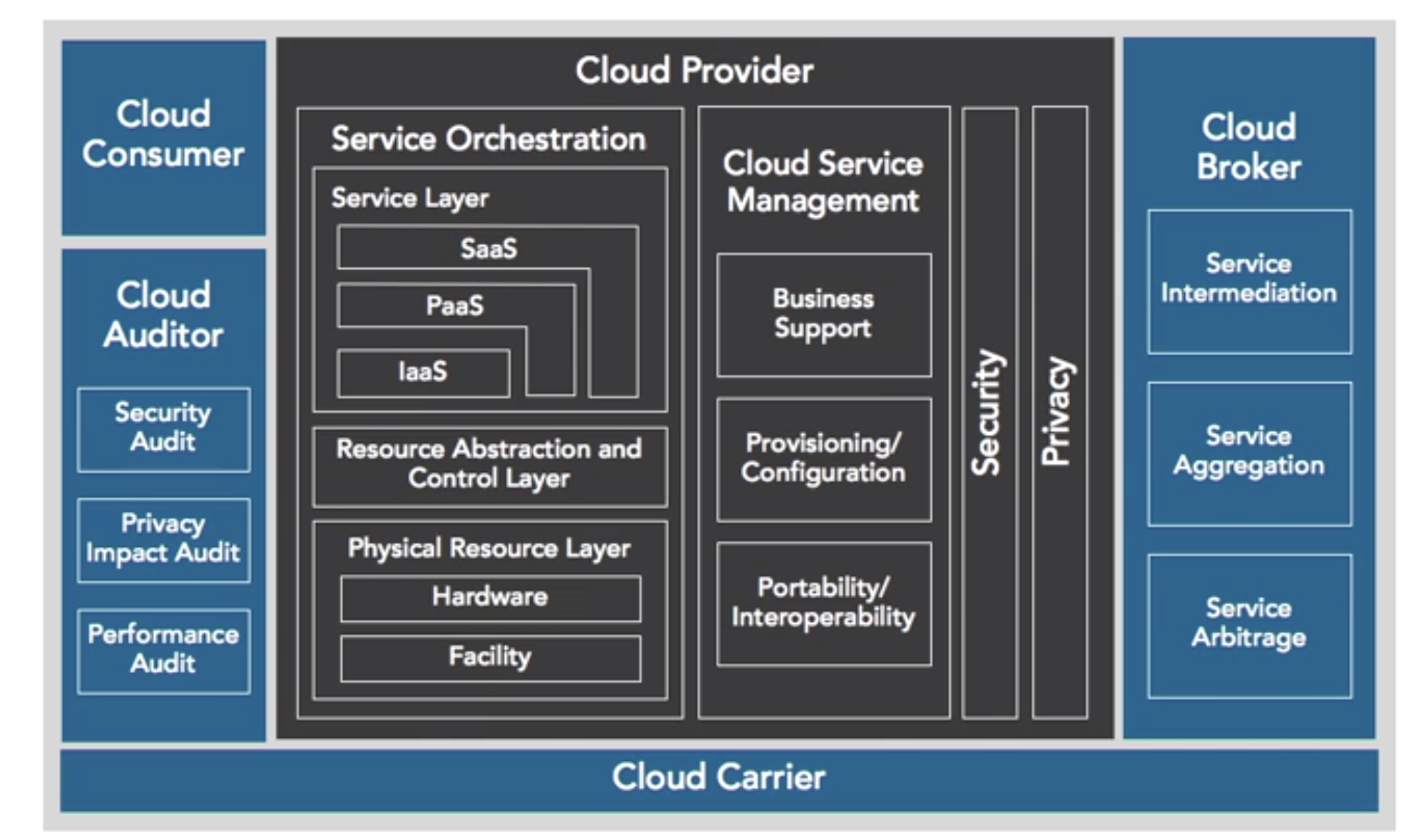 hiwanglong.github.io
hiwanglong.github.io 08_02_Pattern_011_15_Cloud_Computing.png (780×950) | Security
 www.pinterest.com
www.pinterest.com cloud security computing pattern architecture framework practices technology threats services nist sp assessment implementation business mobile
Cloud Computing Security Reference Architecture [4] | Download
![Cloud Computing Security Reference Architecture [4] | Download](https://www.researchgate.net/profile/Jvijaya_Chandra/publication/289985515/figure/fig1/AS:316763976814592@1452533825389/Cloud-Computing-Security-Reference-Architecture-4.png) www.researchgate.net
www.researchgate.net computing
[PDF] On-Demand Security Architecture For Cloud Computing | Semantic
![[PDF] On-Demand Security Architecture for Cloud Computing | Semantic](https://d3i71xaburhd42.cloudfront.net/115193759bcf8ffcb2cf8d8a29cabbf54228fbc3/3-Figure3-1.png) www.semanticscholar.org
www.semanticscholar.org computing
Cloud Computing Architecture Regarding Services 1 Download - Riset
 www.riset.guru.pubiway.com
www.riset.guru.pubiway.com Cloud Computing Security Services Architecture | Download Scientific
 www.researchgate.net
www.researchgate.net [PDF] On-Demand Security Architecture For Cloud Computing | Semantic
![[PDF] On-Demand Security Architecture for Cloud Computing | Semantic](https://d3i71xaburhd42.cloudfront.net/115193759bcf8ffcb2cf8d8a29cabbf54228fbc3/2-Figure1-1.png) www.semanticscholar.org
www.semanticscholar.org Security Architecture Of Cloud Computing [39] | Download Scientific Diagram
![Security Architecture of Cloud Computing [39] | Download Scientific Diagram](https://www.researchgate.net/profile/Muhammad_Sharif9/publication/289672661/figure/download/fig3/AS:613938056159262@1523385647914/Security-Architecture-of-Cloud-Computing-39.png) www.researchgate.net
www.researchgate.net computing
Cloud Computing Security Architecture [12] | Download Scientific Diagram
![Cloud Computing Security Architecture [12] | Download Scientific Diagram](https://www.researchgate.net/profile/Sarfraz-Brohi/publication/257996696/figure/fig2/AS:667714188226583@1536206876935/Cloud-Computing-Security-Architecture-12.jpg) www.researchgate.net
www.researchgate.net Architecture Of Cloud Computing - GeeksforGeeks
 www.geeksforgeeks.org
www.geeksforgeeks.org computing geeksforgeeks
Introduction To Cloud Security Architecture From A Cloud Consumer's
/filters:no_upscale()/articles/cloud-security-architecture-intro/en/resources/fig 2.jpg) www.infoq.com
www.infoq.com Introduction To Cloud Security Architecture From A Cloud Consumer's
/filters:no_upscale()/articles/cloud-security-architecture-intro/en/resources/fig 1.jpg) www.infoq.com
www.infoq.com capabilities
(PDF) Security Architecture Of Cloud Computing
 www.researchgate.net
www.researchgate.net computing vuyyuru reddy
Introduction To Cloud Security Architecture From A Cloud Consumer's
/filters:no_upscale()/articles/cloud-security-architecture-intro/en/resources/fig 4.jpg) www.infoq.com
www.infoq.com Cloud Computing Security Architecture | Download Scientific Diagram
 www.researchgate.net
www.researchgate.net Technology: Cloud Computing History | Key Characteristics Of Cloud
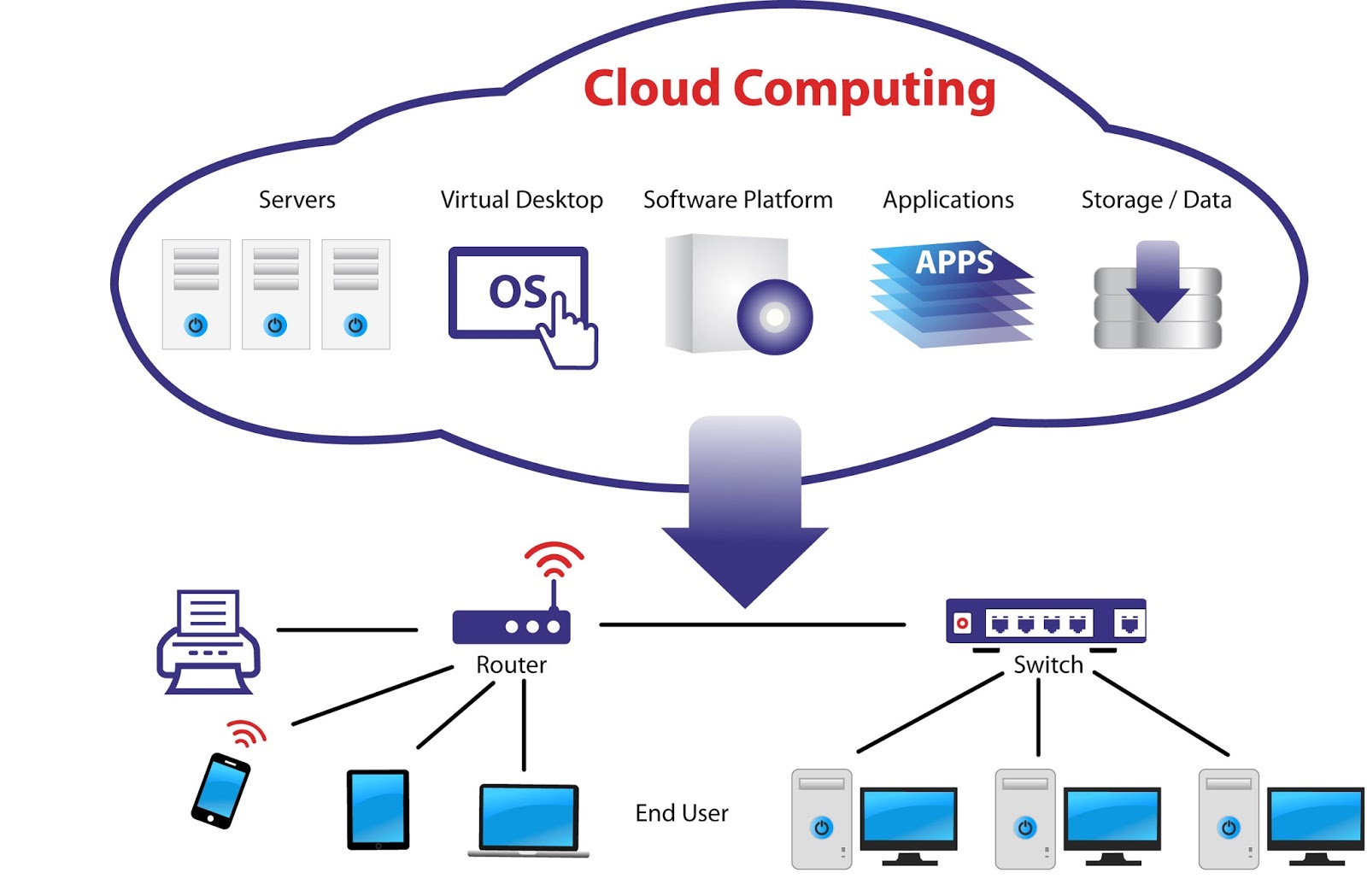 allatesttechnology.blogspot.com
allatesttechnology.blogspot.com cloud computing services system server web architecture history based characteristics training systems technology data software business figure company database management
(PDF) Security Architecture Of Cloud Computing
 www.researchgate.net
www.researchgate.net cloud architecture security computing pdf
Identify The Components Of Your Cloud Security Architecture | Info-Tech
 www.infotech.com
www.infotech.com Cloud Computing Security Reference Architecture | Download Scientific
 www.researchgate.net
www.researchgate.net security computing
Maturing component rapidly enterprise. Cloud architecture security computing pdf. Introduction to cloud security architecture from a cloud consumer's
Post a Comment for "cloud computing security architecture pdf Backend computing"