Managing the Impact of Cloud Computing - The CPA Journal:
Unlocking the Potential of Cloud Computing

The advent of cloud computing has revolutionized the way businesses operate, providing an array of opportunities to streamline operations, enhance collaboration, and reduce costs. As technology continues to evolve at a rapid pace, it is imperative for CPAs and professionals alike to understand the intricacies and challenges associated with this transformative technology.
Cloud computing offers numerous benefits, from increased scalability and flexibility to improved data accessibility. However, with great convenience comes great responsibility. It is essential for organizations to address the following key challenges and devise effective strategies to overcome them:
1. Data Security and Privacy
One of the foremost concerns associated with cloud computing is data security and privacy. As organizations shift their sensitive data to the cloud, they must ensure that robust security measures are in place to protect against potential breaches. Implementing encryption, multi-factor authentication, and regular security audits can bolster the security posture of cloud-based systems.
2. Compliance and Regulatory Requirements

Compliance with industry-specific regulations and data protection laws poses another challenge in cloud computing. Organizations must navigate a complex maze of requirements pertaining to data residency, cross-border data transfers, and customer consent. By partnering with cloud service providers that adhere to stringent compliance standards, organizations can mitigate the risk of non-compliance.
3. Vendor Lock-In

Vendor lock-in refers to the dependence on a particular cloud service provider and the challenges associated with transitioning to an alternative platform. To address this concern, organizations should carefully evaluate the terms of service and contractual agreements when selecting a cloud provider. Implementing a multi-cloud or hybrid cloud strategy can also provide flexibility and mitigate the risk of vendor lock-in.
4. Data Loss and Disaster Recovery

Despite the robust infrastructure and redundancy mechanisms offered by cloud providers, the risk of data loss and service outages still exists. Organizations should establish comprehensive data backup and disaster recovery plans to ensure business continuity. Regular testing and monitoring of these plans are crucial to identify any vulnerabilities and address them promptly.
5. Cost Optimization

While the cloud can offer significant cost savings, improper usage and lack of optimization can lead to unexpected expenses. It is essential for organizations to regularly review their cloud infrastructure, identify unused resources, and optimize their usage to minimize costs. Implementing tools and monitoring mechanisms can aid in efficient resource allocation and cost management.
As organizations embrace the potential of cloud computing, it is crucial to address these challenges and develop effective strategies to overcome them. By prioritizing data security, compliance, vendor management, disaster recovery, and cost optimization, businesses can unlock the true power of the cloud while mitigating associated risks.
If you are searching about Cloud Security Checklist - Express Information Systems you've came to the right web. We have 35 Pictures about Cloud Security Checklist - Express Information Systems like Cloud Computing Security Policy Example / Managing the Impact of Cloud, Cloud Security Checklist and also Home - KRYPSYS. Here you go:
Cloud Security Checklist - Express Information Systems
 www.expressinfo.com
www.expressinfo.com Checklist To Implement Cloud Security In Business Cloud Computing
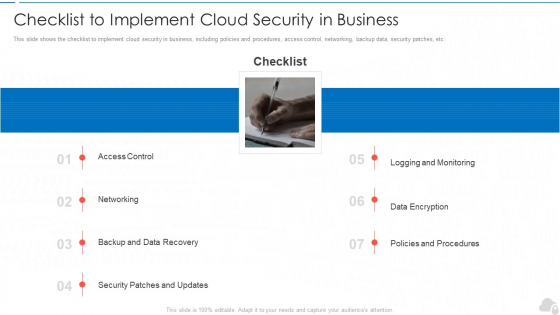 www.slidegeeks.com
www.slidegeeks.com 5 Steps To Cloud Security - The Essential Checklist For Cloud Security
 www.ccsinet.com
www.ccsinet.com cloud checklist security essential computing
Pin On Cloud Computing
 www.pinterest.com
www.pinterest.com cloud checklist security multi choose board
Cloud App Security Checklist | Google & Microsoft 365 Security
 get.managedmethods.com
get.managedmethods.com checklist
Cloud Security Checklist – Cloud Invent
 cloudinvent.com
cloudinvent.com cloud security checklist yuli
Cloud Computing Checklist
 pt.slideshare.net
pt.slideshare.net checklist cloud computing slideshares próximos
Cloud Security Assessment | Practical Industrial Internet Of Things
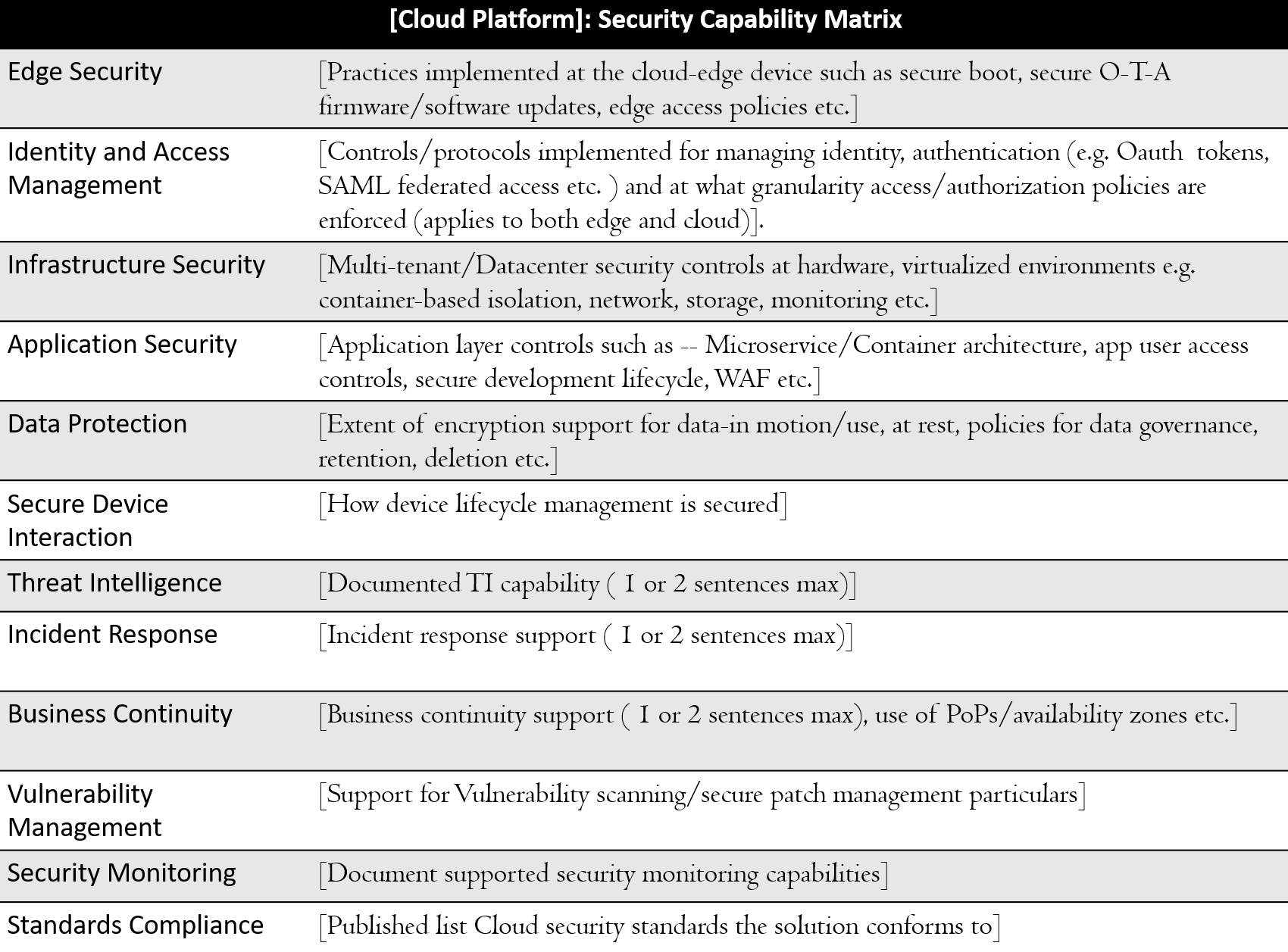 subscription.packtpub.com
subscription.packtpub.com security assessment
Cloud Security: 5 Serious Emerging Cloud Computing Threats To Avoid
 www.thesslstore.com
www.thesslstore.com cloud threats computing security emerging serious avoid
Cloud Computing Security Policy Example / Managing The Impact Of Cloud
 p4nda-teste1.blogspot.com
p4nda-teste1.blogspot.com Exchange Anywhere: Managing Security Risk In The Cloud
 www.anywherexchange.com
www.anywherexchange.com cloud risk security managing
Top 7 Steps Of Cloud Security Checklist To Prevent Any Threats And Risks
 oneclickitconsultancy.wordpress.com
oneclickitconsultancy.wordpress.com Designation: Cloud Administrator – T-Blog
 tekmart.co.za
tekmart.co.za Your Cloud Security Solution Checklist | CloudHealth By VMware
 www.cloudhealthtech.com
www.cloudhealthtech.com Security Audit: Cloud Security Audit Checklist
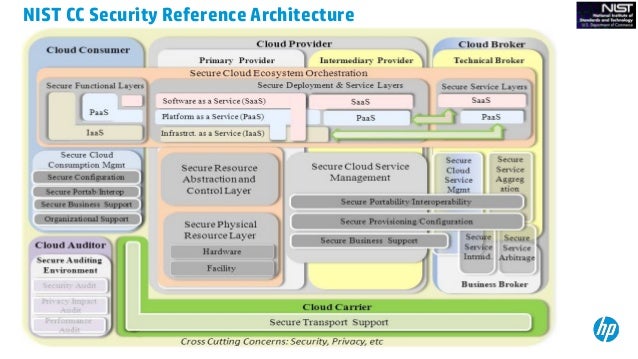 securityauditginkan.blogspot.com
securityauditginkan.blogspot.com audit nist risk evaluating enterprise
Pin On Web Hosting
 www.pinterest.com
www.pinterest.com geekcrunch
Your 10-Step Cloud Application Security Checklist - ManagedMethods
 managedmethods.com
managedmethods.com checklist application
Cloud Security: The Essential Checklist - SkyFlok
 www.skyflok.com
www.skyflok.com cloud checklist security essential
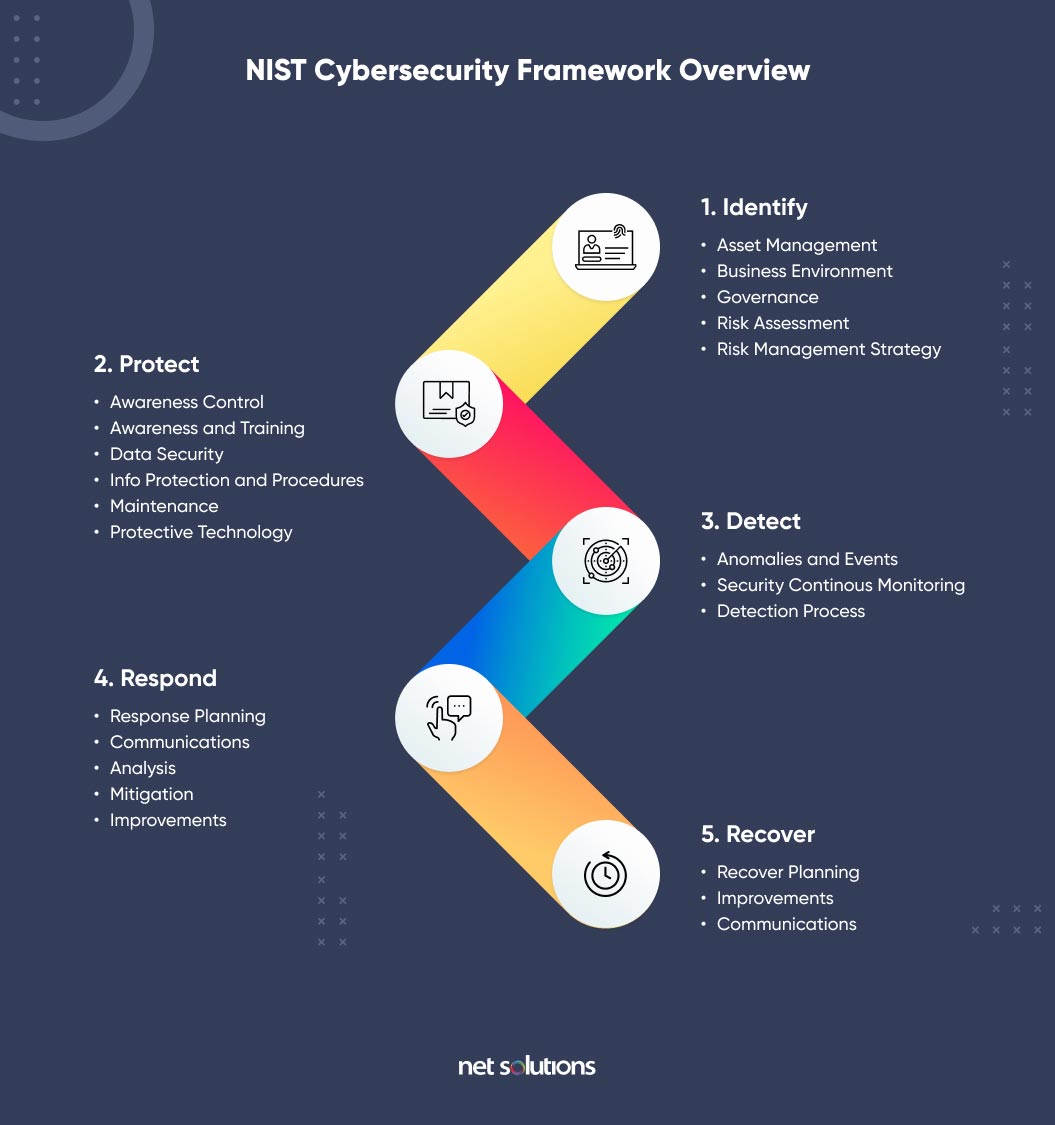
9 Key Cloud Security Challenges And How To Overcome Them
 www.netsolutions.com
www.netsolutions.com nist cybersecurity checklist
Best Practices For Data Security In Cloud Computing | TurningCloud
 www.turningcloud.com
www.turningcloud.com maturing component rapidly enterprise
What Is Cloud Security Monitoring? A Complete Guide
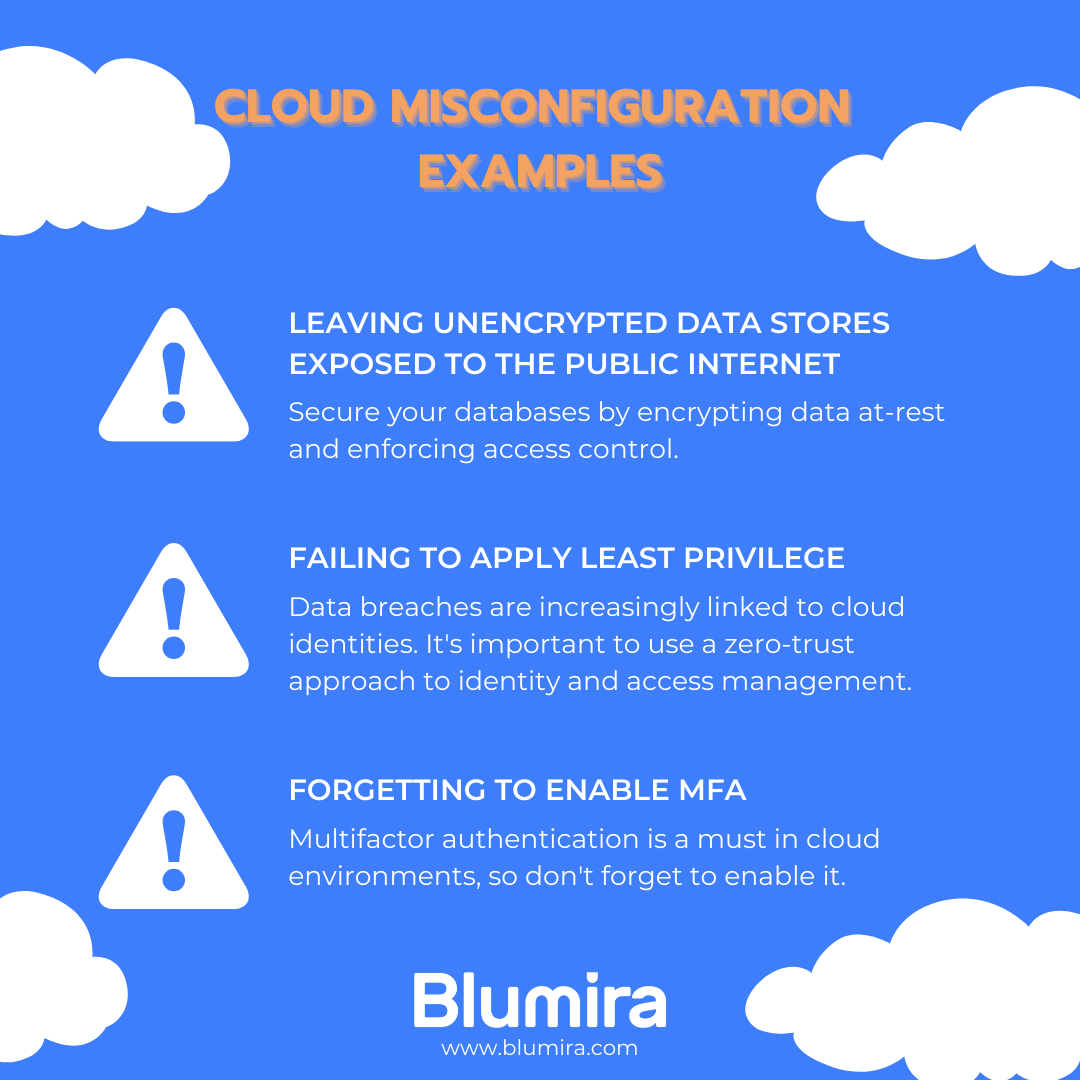 www.blumira.com
www.blumira.com A Security Checklist For Cloud Models - MeshIP Blog
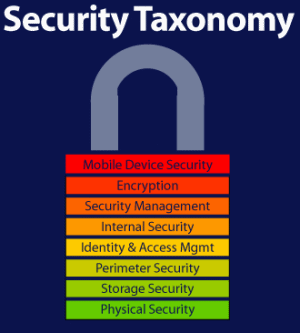 meship.com
meship.com security cloud models checklist saas iaas paas computing taxonomy apply question address five does listing
Cloud Audit Controls: Solutions Checklist
 www.cloudauditcontrols.com
www.cloudauditcontrols.com nist checklist spreadsheet rev audit solutions fips applications tarifas
Checklist For Competent Cloud Security Management
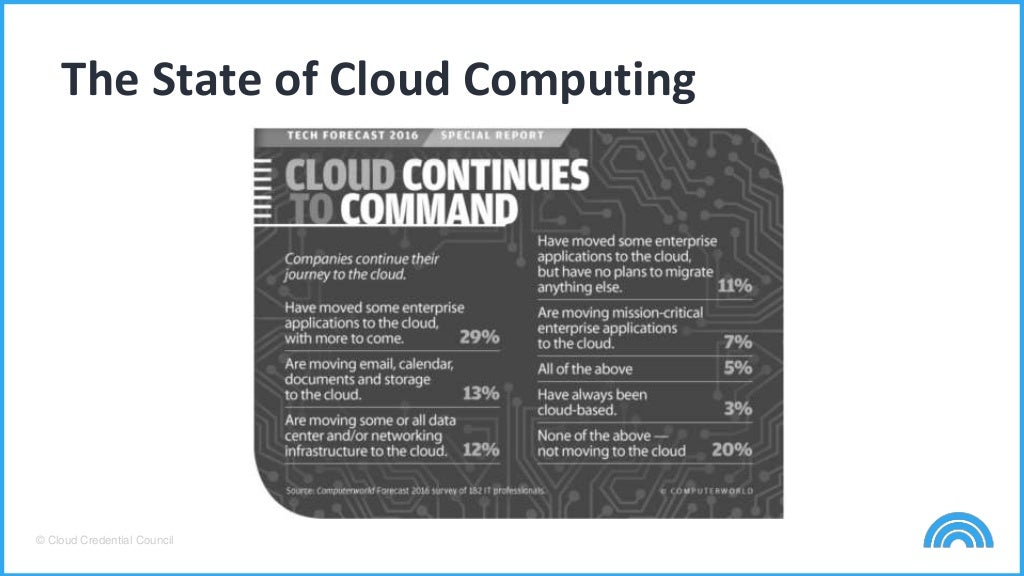 www.slideshare.net
www.slideshare.net competent
Checklist For Competent Cloud Security Management
 www.slideshare.net
www.slideshare.net competent competencies
Cloud Security - Cloud Computing Security - Checklist
 www.isocertificationtrainingcourse.org
www.isocertificationtrainingcourse.org security cloud checklist computing
Resources: Webcasts, Videos, Ebooks & More - Lacework
 www.lacework.com
www.lacework.com lacework
CIO Cloud Security Checklist
 www.slideshare.net
www.slideshare.net security checklist cloud cio slideshare data upcoming
A Comprehensive Guide To Cloud Security In 2022
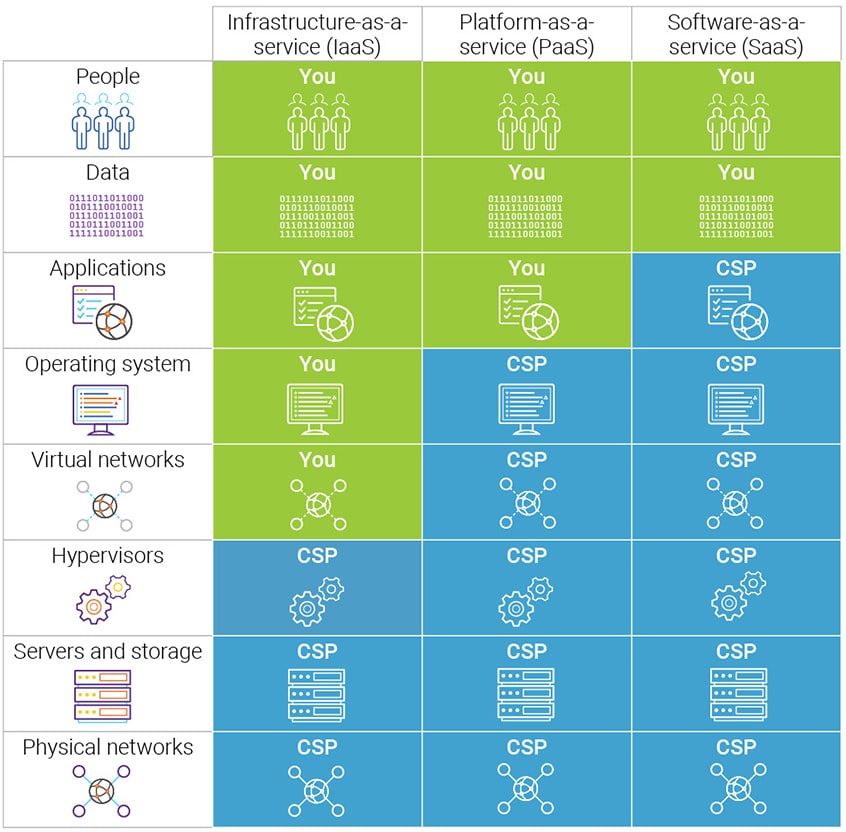 kinsta.com
kinsta.com synopsys sicherheit csp identidad okta gedeelde verantwoordelijkheid practices verantwortung gemeinsame responsible owns kinsta
Home - KRYPSYS
 www.krypsys.com
www.krypsys.com security checklist cloud
IT Security Checkup | Frimley Computing
 www.frimley-computing.com
www.frimley-computing.com security uscj frimley computing practice
Cloud Data Protection| Cloud Security Checklist | Secure Cloud
 www.youtube.com
www.youtube.com cloud security computing secure protection data
Cloud Security Checklist
 spinbackup.com
spinbackup.com checklist spinbackup
Checklist While Choosing Managed Cloud Storage Provider! | Webwerks
 www.webwerks.in
www.webwerks.in cloud managed choosing checklist while storage blogs provider
Managing The Impact Of Cloud Computing - The CPA Journal
 www.cpajournal.com
www.cpajournal.com cloud computing impact risk assessment roles responsibilities cpa managing management provider change document operations shared business analysis
Managing the impact of cloud computing. Cloud threats computing security emerging serious avoid. A security checklist for cloud models
Post a Comment for "cloud computing security checklist Security checklist cloud"