Hey there!
Introducing the DoD Cloud Computing Security Requirements Guide (SRG) Version 1
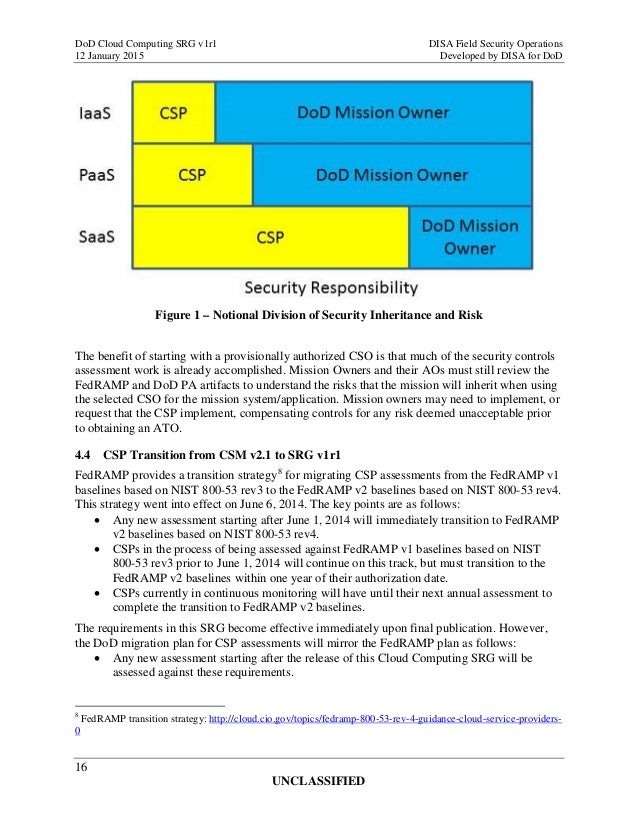
In the world of cloud computing, security is paramount. That's where the Department of Defense Cloud Computing Security Requirements Guide (SRG) Version 1 comes into play. This comprehensive guide provides organizations with the necessary requirements to ensure the security of their cloud computing systems.
The DoD Cloud Computing SRG Version 1 covers a wide range of security aspects, including network security, access control, data protection, and much more. By following these guidelines, businesses can enjoy the benefits of cloud computing while keeping their sensitive information safe and secure.
Why is cloud security important?
With the increasing popularity of cloud computing, the need for robust security measures is more important than ever. Cloud computing allows businesses to store and access their data on remote servers, providing flexibility, scalability, and cost-effectiveness. However, this also means that sensitive information is stored outside of the traditional data center, making it more vulnerable to cybersecurity threats.
By implementing the guidelines outlined in the DoD Cloud Computing SRG Version 1, organizations can safeguard their data from unauthorized access, breaches, and other cyber threats. This guide acts as a comprehensive roadmap for businesses looking to leverage the benefits of cloud computing without compromising on security.
Discover the Best Cloud Security Companies

Now that you're aware of the importance of cloud security, let's explore some of the best cloud security companies in the industry. These companies specialize in providing top-notch security solutions that protect your data in the cloud.
1. Company XYZ
With a proven track record in the cloud security industry, Company XYZ offers a range of services designed to address the unique security challenges faced by businesses today. Their team of experts works tirelessly to stay ahead of emerging threats and provide innovative solutions to keep your cloud infrastructure secure.
2. SecureCloud
SecureCloud is a leading provider of cloud security solutions, offering cutting-edge technologies that secure your data and applications in the cloud. Their comprehensive suite of services includes real-time threat monitoring, data encryption, access control, and much more.
3. CloudDefender
CloudDefender takes cloud security to the next level with their advanced threat intelligence and proactive monitoring. They offer a range of services, including vulnerability assessments, security incident response, and continuous security monitoring, to ensure your cloud environment is always protected.
Whether you're a small startup or a large enterprise, these cloud security companies have the expertise and tools to safeguard your valuable data in the cloud. Don't compromise on security – choose a trusted partner that prioritizes the safety of your information.
In conclusion, cloud security is of utmost importance in today's digital landscape. The DoD Cloud Computing Security Requirements Guide (SRG) Version 1 provides businesses with the necessary guidelines to ensure their cloud computing systems are secure. Additionally, there are several reputable cloud security companies available who specialize in protecting your data and applications in the cloud. Remember, investing in robust cloud security measures can save your business from potential data breaches and cyber threats. Stay secure, stay protected!
If you are searching about Cloud Computing Security Requirements | Download Scientific Diagram you've came to the right web. We have 35 Images about Cloud Computing Security Requirements | Download Scientific Diagram like Cloud Security Demystified - Small Business Trends, Global SLA NFV | Pipeline Magazine | OSS and BSS News and Info and also Best Practices for Data Security in Cloud Computing | TurningCloud. Read more:
Cloud Computing Security Requirements | Download Scientific Diagram
 www.researchgate.net
www.researchgate.net Special Requirements For Data Security In The Cloud | Cloud Computing
 in.pinterest.com
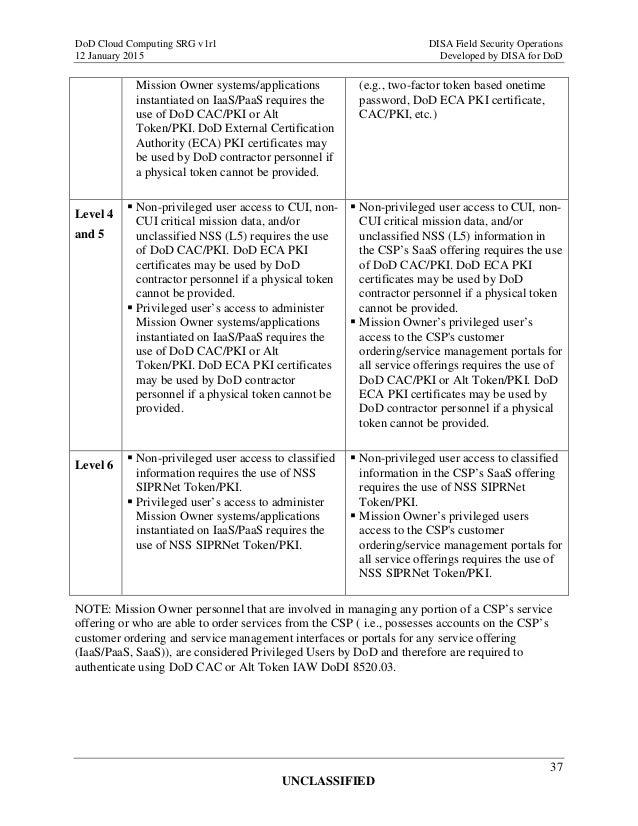
in.pinterest.com Do D Cloud Computing Security Requirements Guide (srg) Version 1
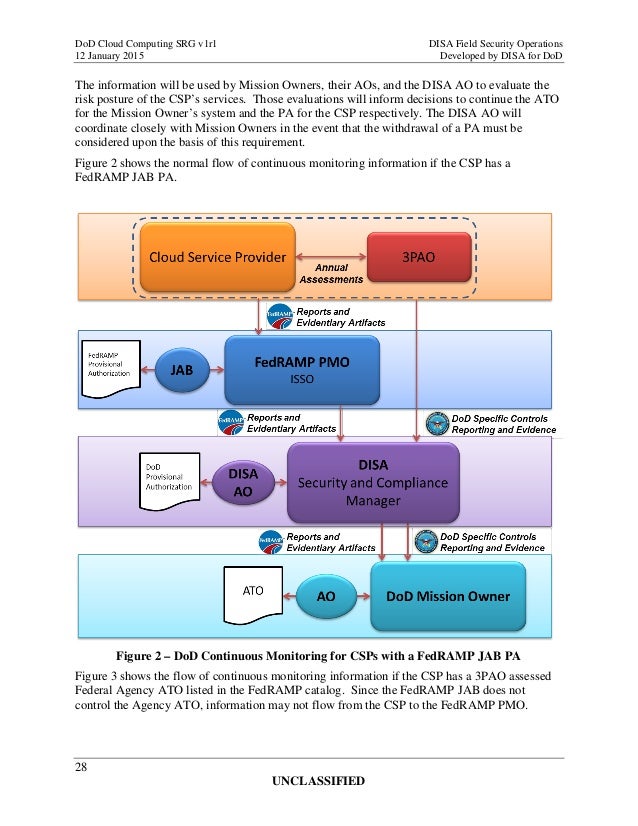 www.slideshare.net
www.slideshare.net srg
(PDF) Cloud Computing Security: A Survey
 www.researchgate.net
www.researchgate.net computing cloud survey security
Do D Cloud Computing Security Requirements Guide (srg) Version 1
 www.slideshare.net
www.slideshare.net srg
Document Moved
 www.docusnap.com
www.docusnap.com requirements computing increases security cloud docusnap
Best Practices For Data Security In Cloud Computing | TurningCloud
 www.turningcloud.com
www.turningcloud.com maturing component rapidly enterprise
Do D Cloud Computing Security Requirements Guide (srg) Version 1
 www.slideshare.net
www.slideshare.net srg
Do D Cloud Computing Security Requirements Guide (srg) Version 1
 www.slideshare.net
www.slideshare.net computing srg
A Comprehensive Guide To Cloud Security In 2023
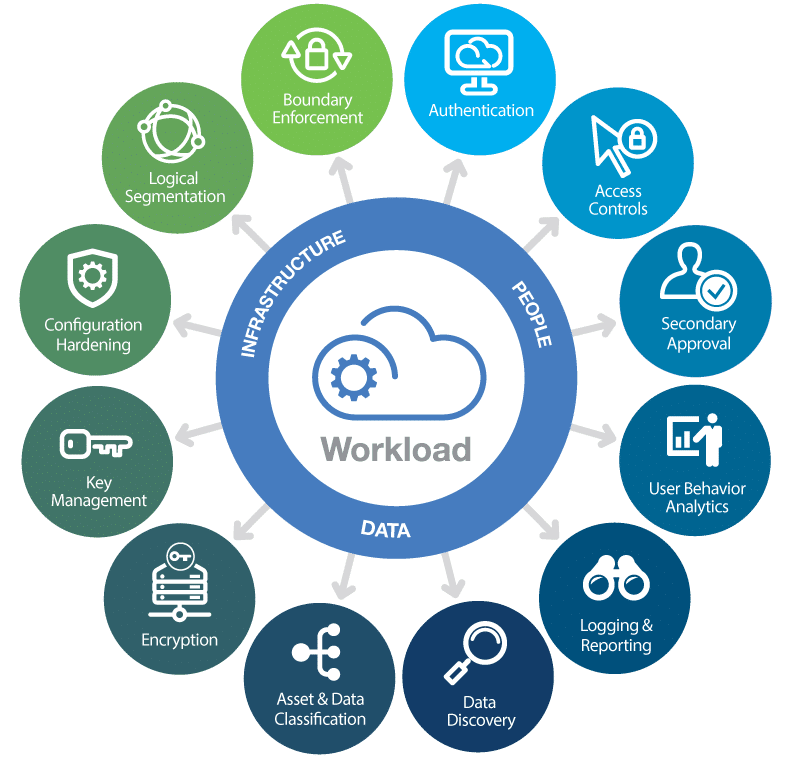 kinsta.com
kinsta.com workloads connectivity sicherheit azure compliance hytrust securing absicherung beveiligen devops pipeline devsecops carichi practices kinsta clicdata edge neglect
DoD Cloud Computing Security Requirements Guide (SRG) Version 1
 publicintelligence.net
publicintelligence.net dod srg publicintelligence cloudsecurity
(PDF) Cloud Computing Security Issues And Challenges: A Survey
 www.researchgate.net
www.researchgate.net computing survey
Cloud Security Demystified - Small Business Trends
 smallbiztrends.com
smallbiztrends.com computing smallbiztrends demystified policy
Top 5 Cloud Computing Security Concerns - Driz Group
 www.drizgroup.com
www.drizgroup.com security computing cloud concerns medicaid provider
Security Requirement Specification Model For Cloud Computing Services
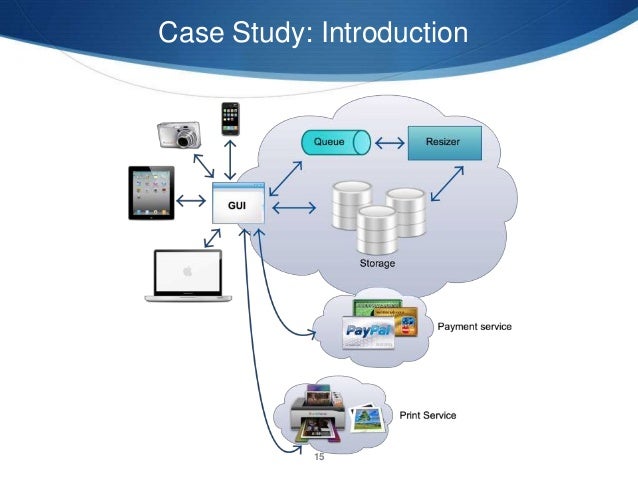 www.slideshare.net
www.slideshare.net Do D Cloud Computing Security Requirements Guide (srg) Version 1
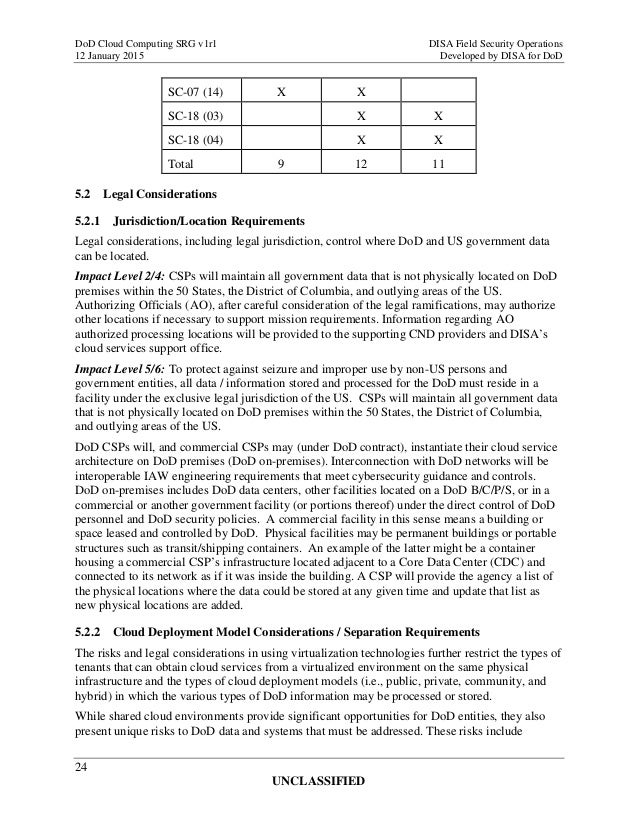 www.slideshare.net
www.slideshare.net srg
Global SLA NFV | Pipeline Magazine | OSS And BSS News And Info
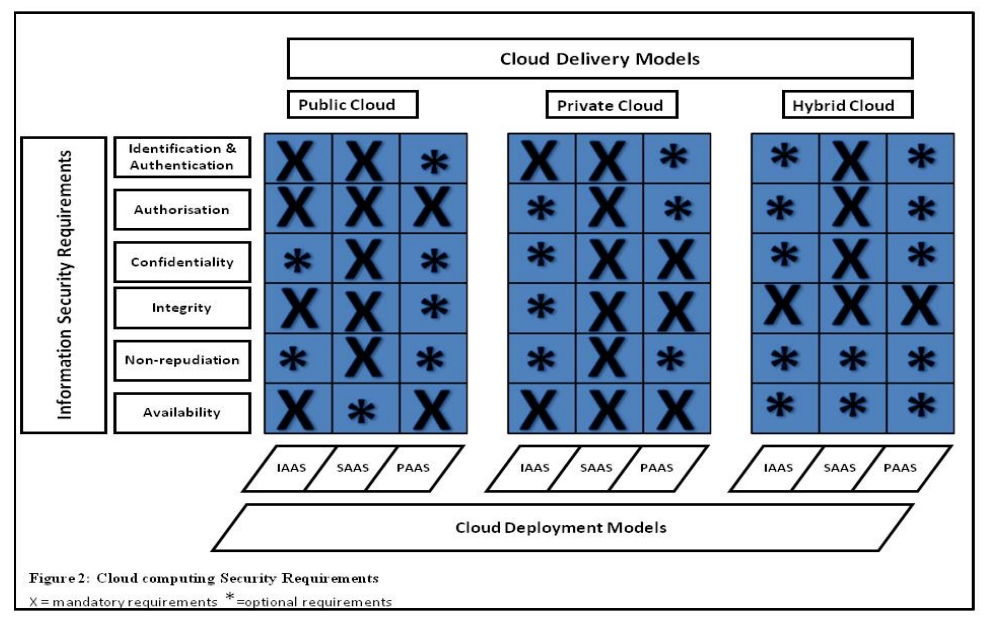 www.pipelinepub.com
www.pipelinepub.com cloud computing security requirements platform figure source
Ultimate Guide To Cloud Computing Security- Hire Cloud Expert | Chapter247
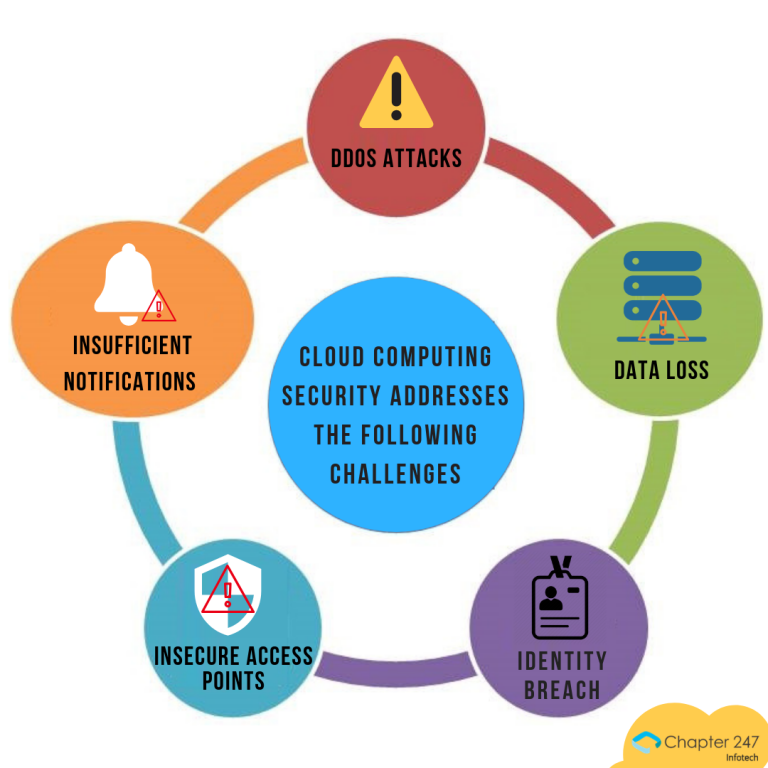 www.chapter247.com
www.chapter247.com chapter247 ddos attacks
Do D Cloud Computing Security Requirements Guide (srg) Version 1
 www.slideshare.net
www.slideshare.net computing srg requirements
DoD Cloud Computing Security Requirements | Schellman
 www.schellman.com
www.schellman.com Cloud Computing Security And Your Applications - DZone
 dzone.com
dzone.com dzone
Do D Cloud Computing Security Requirements Guide (srg) Version 1
 www.slideshare.net
www.slideshare.net computing srg
Design-for-pets: Best Cloud Security Companies
 design-for-pets.blogspot.com
design-for-pets.blogspot.com DISA Releases New Cloud Security Requirement Guide - FedScoop
 www.fedscoop.com
www.fedscoop.com cloud security disa requirements guide fedramp diagram fedscoop requirement releases agency showing work
Do D Cloud Computing Security Requirements Guide (srg) Version 1
 www.slideshare.net
www.slideshare.net srg requirements
Do D Cloud Computing Security Requirements Guide (srg) Version 1
 www.slideshare.net
www.slideshare.net srg
Cloud Computing Security Requirements Guide | Cybersecurity Automation
 www.cybersecurity-automation.com
www.cybersecurity-automation.com Ultimate Guide To Cloud Computing Security- Hire Cloud Expert | Chapter247
 www.chapter247.com
www.chapter247.com cloud security computing ultimate guide understand let detail
Cloud Security: Guide To Secure Cloud Computing -RK Infotech
 www.rkinfotechindia.com
www.rkinfotechindia.com Cloud Computing Security Requirement Figure 2, Illustrating The
 www.researchgate.net
www.researchgate.net computing illustrating requirement shivlal mewada
Do D Cloud Computing Security Requirements Guide (srg) Version 1
 www.slideshare.net
www.slideshare.net srg
Do D Cloud Computing Security Requirements Guide (srg) Version 1
 www.slideshare.net
www.slideshare.net srg
Do D Cloud Computing Security Requirements Guide (srg) Version 1
 www.slideshare.net
www.slideshare.net srg requirements
Cloud Computing Security Requirements | Download Scientific Diagram
 www.researchgate.net
www.researchgate.net Do D Cloud Computing Security Requirements Guide (srg) Version 1
 www.slideshare.net
www.slideshare.net srg requirements dod release
Computing srg. Best practices for data security in cloud computing. Do d cloud computing security requirements guide (srg) version 1
Post a Comment for "cloud computing security requirements guide Cloud computing security requirements"