Cloud security is a topic that has gained significant attention in recent years. With the increasing reliance on cloud computing services, it has become essential for businesses, especially small ones, to understand and implement robust security measures to protect their data and systems. In this post, we will demystify cloud security and provide you with guidance on how to ensure the security of your cloud-based infrastructure.
Understanding the Basics of Cloud Security
In simple terms, cloud security refers to the set of procedures, protocols, and technologies designed to protect data and applications stored in the cloud. It involves managing and controlling access to data, ensuring its confidentiality, integrity, and availability, and safeguarding against unauthorized access, data breaches, and other potential threats.
By leveraging cloud computing services, businesses can enjoy numerous benefits such as scalability, cost-effectiveness, and increased productivity. However, there are also potential risks associated with cloud computing, including data breaches, unauthorized access, and service disruptions. Implementing effective cloud security measures is crucial to mitigating these risks and ensuring the safety of your business-critical information.
Best Practices for Cloud Security
When it comes to cloud security, there are several best practices that businesses should follow, regardless of their size or industry. These practices include:

1. Strong Authentication and Access Controls
Implementing strong authentication mechanisms, such as multifactor authentication, can significantly enhance the security of your cloud infrastructure. In addition, adopting granular access controls ensures that only authorized individuals can access sensitive data and applications.
2. Regular Security Audits and Assessments
Performing security audits and assessments on a regular basis helps identify potential vulnerabilities and areas for improvement. Regular audits also help ensure compliance with industry standards and regulations.
3. Data Encryption
Encrypting sensitive data before storing it in the cloud adds an extra layer of protection. Even if a data breach occurs, encrypted data is useless without the corresponding decryption key.
4. Regular Data Backups
Regularly backing up your data is crucial for quick data recovery in the event of data loss or system failures. It ensures that your business can resume its operations with minimal disruption.
5. Employing Secure Data Transmission Protocols
When transmitting data to and from the cloud, ensure that secure protocols, such as HTTPS, are used. This helps protect data from interception and unauthorized access.
Conclusion
As cloud computing continues to revolutionize the way businesses operate, ensuring the security of cloud-based infrastructure becomes paramount. By following best practices such as strong authentication, regular audits, data encryption, data backups, and secure data transmission protocols, businesses can significantly reduce the risks associated with cloud computing.
Remember, your data is your most valuable asset, and protecting it should be a top priority. By implementing robust cloud security measures, small businesses can confidently leverage cloud computing services to drive growth and innovation.
If you are looking for Cloud Security - here is what you should know - SuperAdmins you've came to the right web. We have 35 Pics about Cloud Security - here is what you should know - SuperAdmins like Cloud Security Demystified - Small Business Trends, Ultimate Guide to Cloud Computing Security- Hire cloud Expert | Chapter247 and also Research HQ | What is cloud security? How is it different from. Read more:
Cloud Security - Here Is What You Should Know - SuperAdmins
 superadmins.com
superadmins.com Cloud Security Demystified - Small Business Trends
 smallbiztrends.com
smallbiztrends.com computing smallbiztrends demystified policy
Do D Cloud Computing Security Requirements Guide (srg) Version 1
 www.slideshare.net
www.slideshare.net srg requirements dod release
(DoD) CLOUD COMPUTING SECURITY REQUIREMENTS GUIDE
 studylib.net
studylib.net security cloud dod computing guide requirements srg version release defense department data
Security In Cloud Computing - TechVidvan
 techvidvan.com
techvidvan.com Latest Cloud Computing Threats To Organizations & Prevention Strategies
 www.techpluto.com
www.techpluto.com cloud security issues tips computing challenges data threats securing solution information attacks prevention lab organizations strategies latest
Global SLA NFV | Pipeline Magazine | OSS And BSS News And Info
 www.pipelinepub.com
www.pipelinepub.com cloud computing security requirements platform figure source
(PDF) Cloud Computing Security Issues And Challenges: A Survey
 www.researchgate.net
www.researchgate.net computing survey
Document Moved
 www.docusnap.com
www.docusnap.com requirements computing increases security cloud docusnap
DISA Releases New Cloud Security Requirement Guide - FedScoop
 www.fedscoop.com
www.fedscoop.com cloud security disa requirements guide fedramp diagram fedscoop requirement releases agency showing work
Cloud Computing And Security - SecurIT360
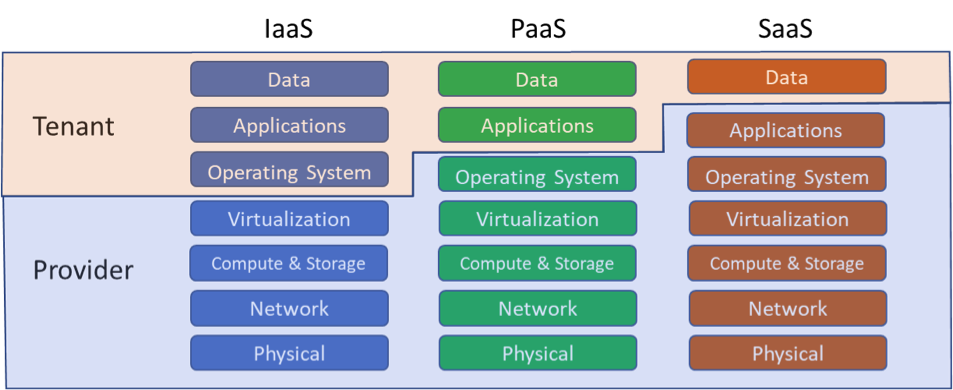 www.securit360.com
www.securit360.com security computing cloud
Do D Cloud Computing Security Requirements Guide (srg) Version 1
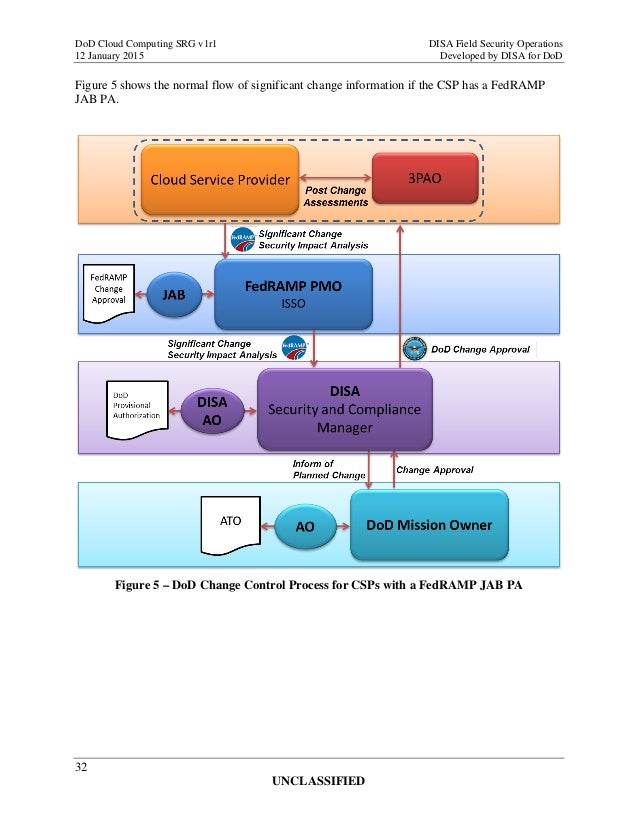 www.slideshare.net
www.slideshare.net computing srg
A Comprehensive Guide To Cloud Security In 2023
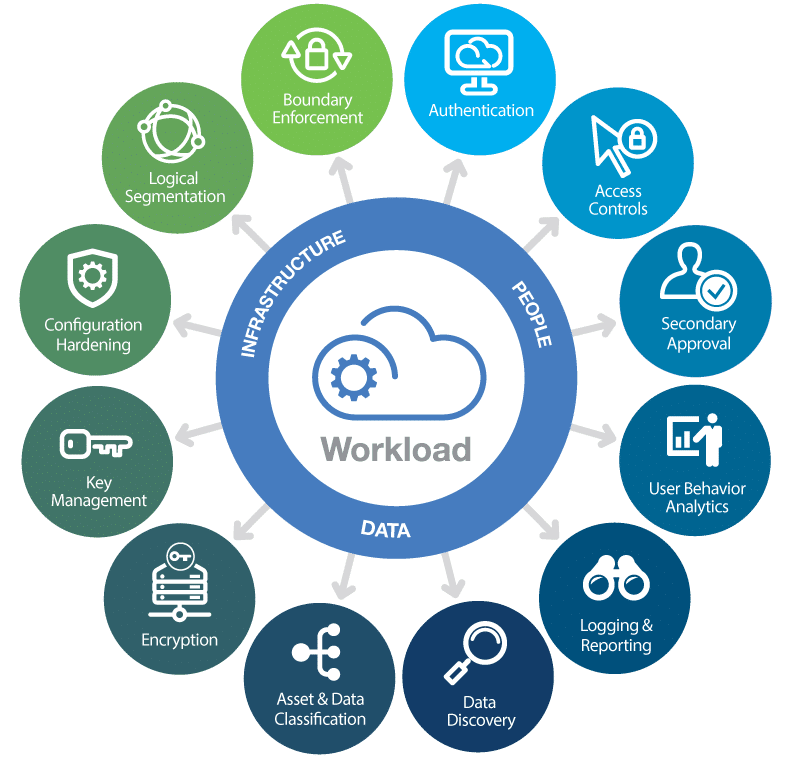 kinsta.com
kinsta.com workloads connectivity sicherheit azure compliance hytrust securing absicherung beveiligen devops pipeline devsecops carichi practices kinsta clicdata edge neglect
(PDF) Cloud Computing Security: A Survey
 www.researchgate.net
www.researchgate.net computing cloud survey security
Do D Cloud Computing Security Requirements Guide (srg) Version 1
 www.slideshare.net
www.slideshare.net srg
Frequently Asked Cloud Computing Interview Questions - Penetration
 reconshell.com
reconshell.com computing
Do D Cloud Computing Security Requirements Guide (srg) Version 1
 www.slideshare.net
www.slideshare.net srg
Cloud Computing Security - Hackonology
 hackonology.com
hackonology.com understanding
Do D Cloud Computing Security Requirements Guide (srg) Version 1
 www.slideshare.net
www.slideshare.net srg requirements
Do D Cloud Computing Security Requirements Guide (srg) Version 1
 www.slideshare.net
www.slideshare.net srg
Cloud Computing Security Requirements | Download Scientific Diagram
 www.researchgate.net
www.researchgate.net Do D Cloud Computing Security Requirements Guide (srg) Version 1
 www.slideshare.net
www.slideshare.net srg
Cloud Computing Security Requirements Guide | Cybersecurity Automation
 www.cybersecurity-automation.com
www.cybersecurity-automation.com ISO 27001-mapping For Integrity Of Cloud Communication Security
 www.researchgate.net
www.researchgate.net requirement integrity
DoD Cloud Computing Security Requirements | Schellman
 www.schellman.com
www.schellman.com (PDF) Cloud Computing Security Requirements: A Systematic Review
 www.researchgate.net
www.researchgate.net requirements security cloud systematic computing review
Cloud Computing Security Requirements | Download Scientific Diagram
 www.researchgate.net
www.researchgate.net Cloud Computing Security And Your Applications - DZone
 dzone.com
dzone.com dzone
Do D Cloud Computing Security Requirements Guide (srg) Version 1
 www.slideshare.net
www.slideshare.net computing srg requirements
The Cloud Security Part 1: For Dummies - IOD: [tech.content]
![The Cloud Security Part 1: For Dummies - IOD: [tech.content]](http://www.iamondemand.com/wp-content/uploads/2011/05/cloud-security-considerations.jpg) www.iamondemand.com
www.iamondemand.com cloud security data considerations dummies part
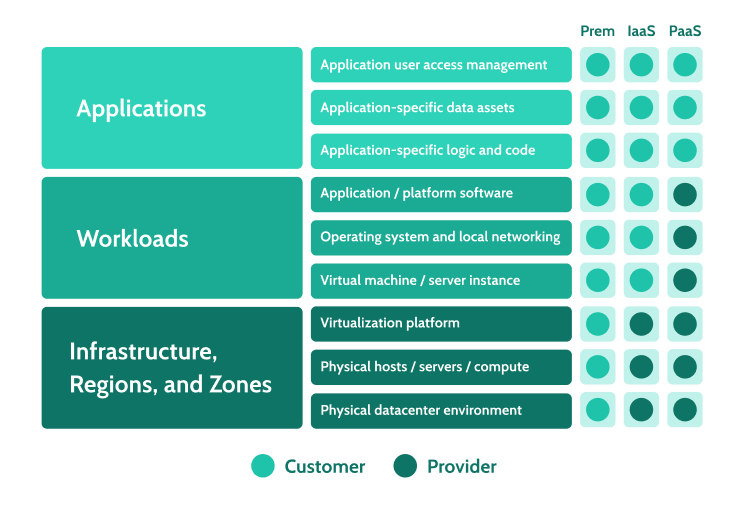
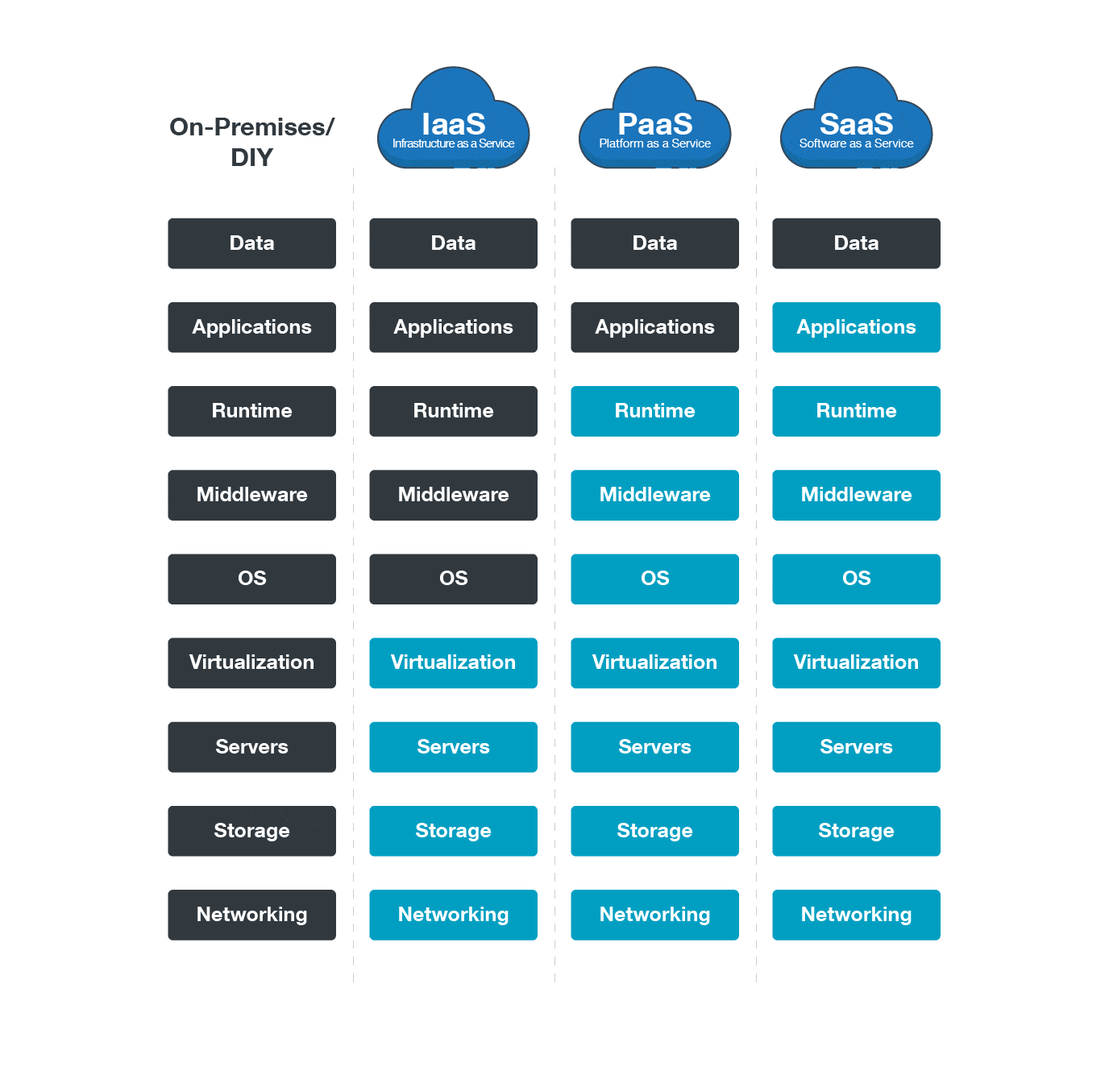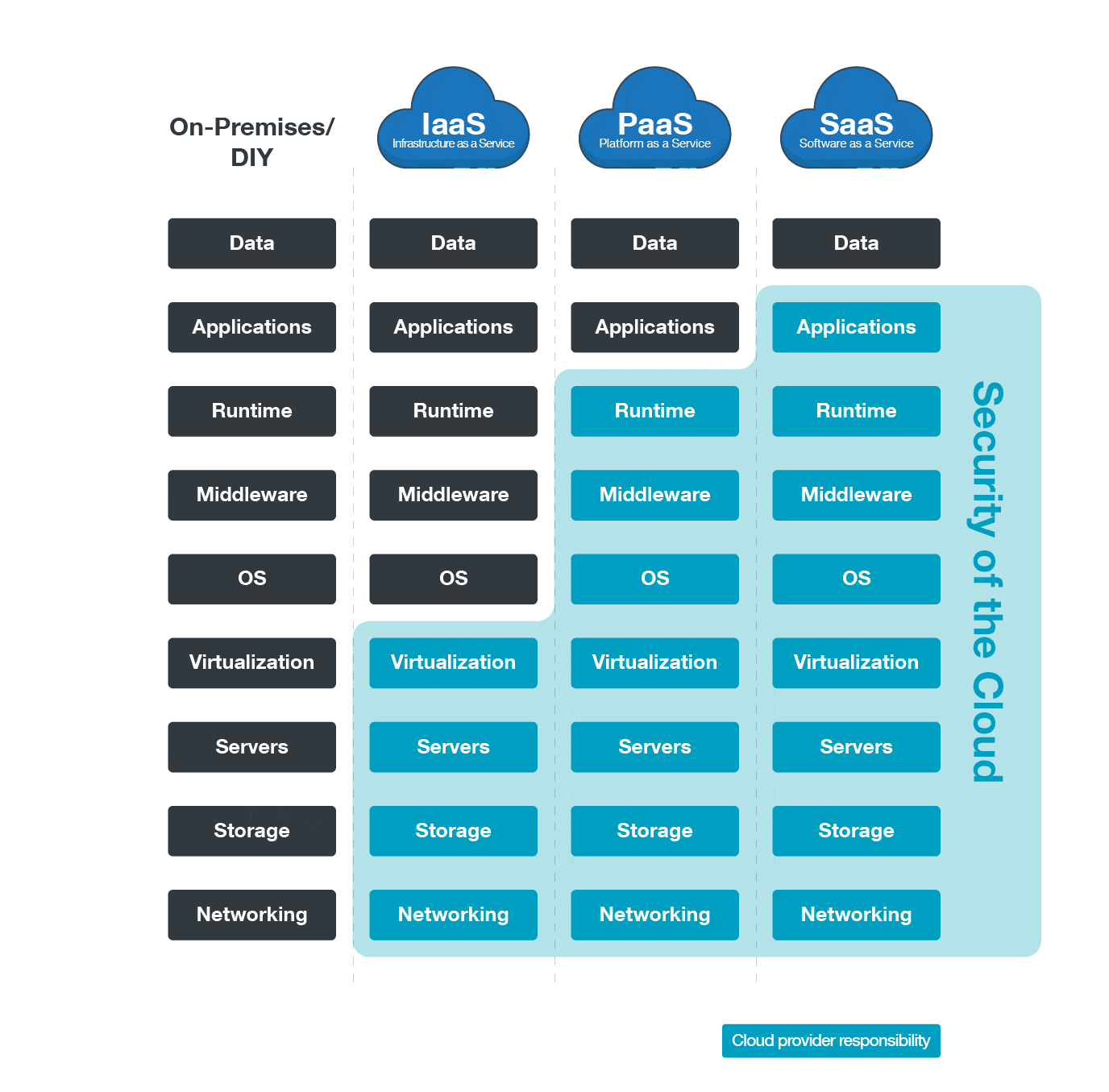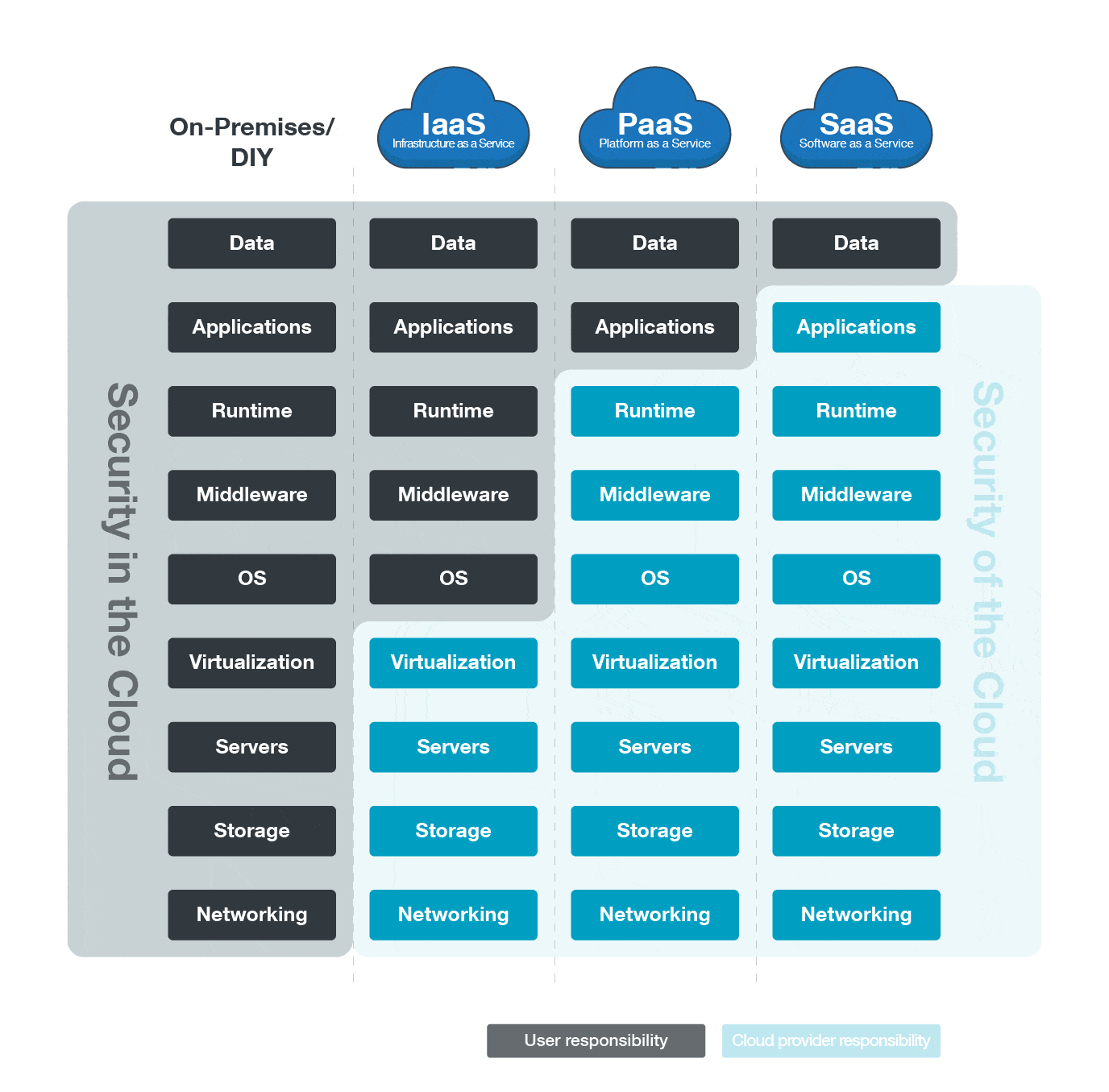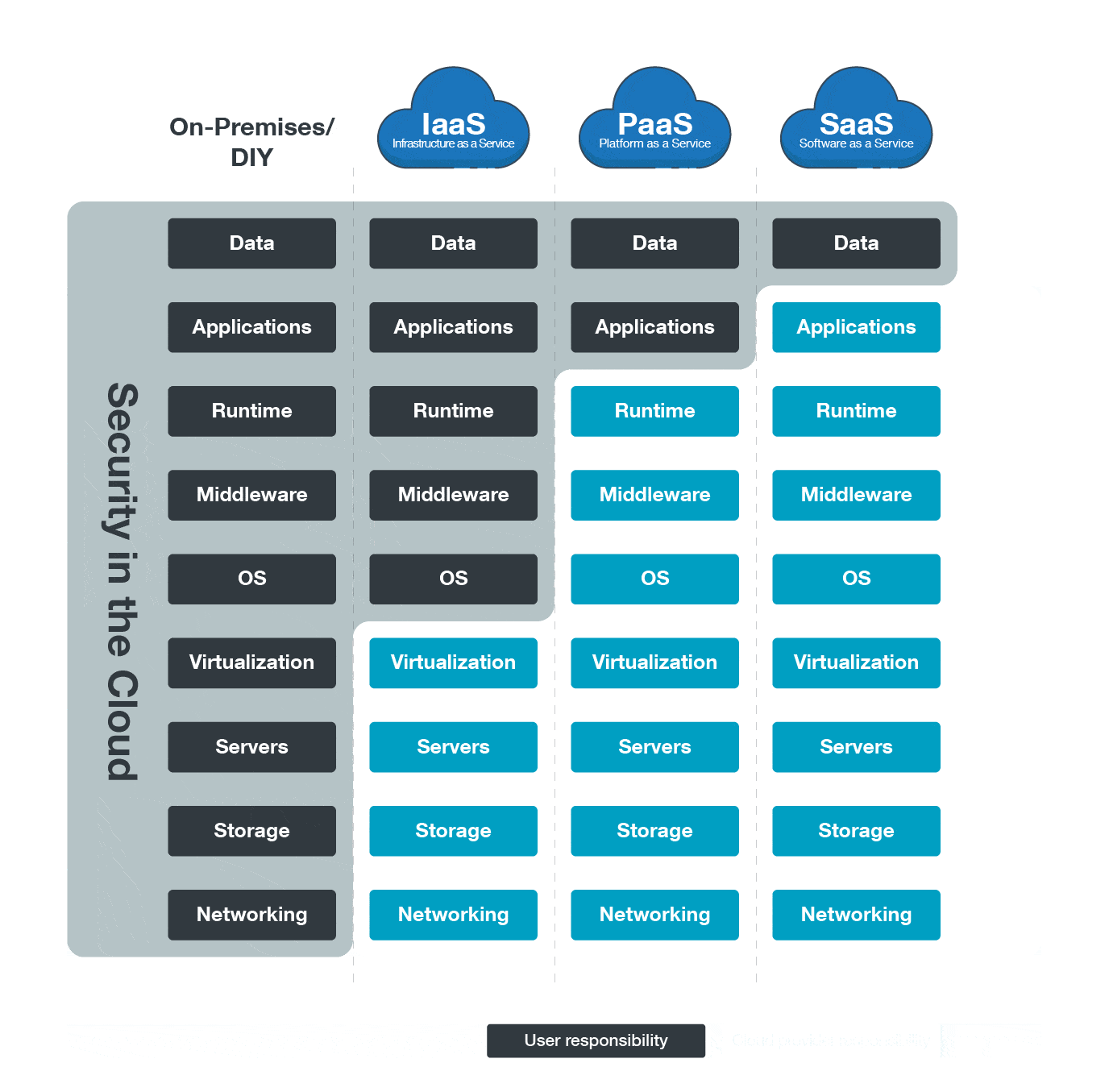
Research HQ | What Is Cloud Security? How Is It Different From
 www.researchhq.net
www.researchhq.net premises researchhq deployment depicted computing characteristics graph
Cloud Computing Security Requirement Figure 2, Illustrating The
 www.researchgate.net
www.researchgate.net computing illustrating requirement shivlal mewada
Ultimate Guide To Cloud Computing Security- Hire Cloud Expert | Chapter247
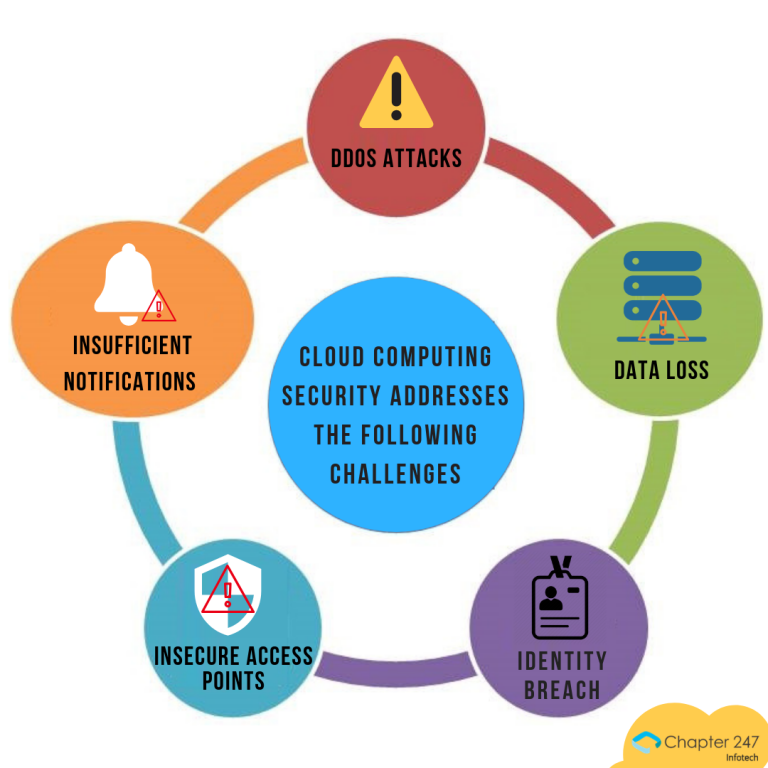 www.chapter247.com
www.chapter247.com chapter247 ddos attacks
(PDF) Cloud Computing Security Requirements: A Systematic Review
 www.researchgate.net
www.researchgate.net security cloud systematic review requirements computing
05 Misconceptions About Cloud Security | Cloud Space Technology Solutions
 cloudspace.vn
cloudspace.vn cloud security misconceptions
Workloads connectivity sicherheit azure compliance hytrust securing absicherung beveiligen devops pipeline devsecops carichi practices kinsta clicdata edge neglect. Global sla nfv. Cloud security data considerations dummies part
Post a Comment for "cloud computing security requirements Requirement integrity"