In recent years, cloud computing has become increasingly prevalent, revolutionizing the way businesses store and access their data. However, with this technological advancement comes a new set of cybersecurity risks that need to be carefully considered. As we delve into the realm of cloud computing, it is crucial to understand the importance of incorporating robust cybersecurity strategies to ensure the protection of sensitive information.
The Risks of Cloud Computing
One of the primary cybersecurity risks associated with cloud computing is data breaches. With data being stored on remote servers rather than on-site, it becomes more vulnerable to unauthorized access by malicious individuals or cybercriminals. This heightened risk emphasizes the need for stringent security measures and encryption protocols to safeguard against potential breaches.
The shared responsibility model is another aspect to consider when assessing cloud computing risks. While cloud service providers do offer security measures, it is important for businesses to understand that they also bear some responsibility in ensuring the integrity and confidentiality of their data. This requires organizations to establish strong internal security protocols and educate employees on best practices for using cloud-based services.
Importance of Cloud Computing in Cybersecurity Strategy
Despite the risks, cloud computing can greatly enhance an organization's overall cybersecurity strategy. By adopting cloud-based solutions, businesses can leverage the expertise and resources of cloud service providers, who specialize in maintaining robust security measures. These providers invest heavily in cybersecurity, ensuring continuous monitoring, regular updates, and adherence to industry standards.
Furthermore, cloud computing offers enhanced data backup and disaster recovery capabilities. In the event of a cybersecurity incident or data loss, businesses can rely on cloud-based backups to restore their systems and recover essential information quickly. This reduces downtime and minimizes the impact of potential cybersecurity breaches.
Best Practices for Cloud Security
Implementing effective cloud security measures requires a proactive approach combined with constant monitoring and analysis. Here are some best practices to consider:
1. Strong Authentication Mechanisms:
Enforce the use of strong, unique passwords and multi-factor authentication. Implementing these measures significantly reduces the risk of unauthorized access to cloud-based systems and data.
2. Regularly Update and Patch:
Stay up-to-date with the latest security patches and software updates. This helps to address any vulnerabilities in cloud-based systems and ensures protection against emerging threats.
3. Encrypt Data:
Encrypting data both during transmission and storage adds an extra layer of protection. This ensures that even if data is intercepted or compromised, it remains unreadable and unusable to unauthorized individuals.
4. Monitor and Analyze:
Implement robust monitoring and analysis tools to detect any abnormal activities or potential cybersecurity threats. These tools can help identify and respond to incidents promptly, reducing the impact on your organization.
The Future of Cloud Computing and Cybersecurity
As technology continues to evolve, so will the nature of cybersecurity risks. Cloud computing is expected to play a vital role in addressing these challenges. With advancements in machine learning and artificial intelligence, cloud service providers are continuously enhancing their security measures to stay ahead of cyber threats.
Additionally, collaboration between businesses, cloud service providers, and cybersecurity experts will be crucial in developing innovative solutions to combat emerging risks. By sharing knowledge and resources, the cybersecurity landscape can be strengthened, ensuring a safer and more secure environment for businesses and individuals alike.
In conclusion, as cloud computing becomes increasingly pervasive, understanding and addressing the cybersecurity risks associated with this technology is paramount. By incorporating robust security measures, businesses can leverage the benefits of cloud computing while minimizing the potential vulnerabilities. This proactive approach will help create a secure and resilient digital infrastructure for businesses to thrive in the digital age.
Sources:
1. "What Are Cybersecurity Risks of Cloud Computing?" - NJBIA. Retrieved from https://njbia.org/wp-content/uploads/2021/07/052918_NJBT_Cloud_Security-675x380.jpg
2. "The Importance of Cloud Computing in Your Cybersecurity Strategy." Retrieved from https://cybersainik.com/wp-content/uploads/2021/07/The-Importance-of-Cloud-Computing-in-Your-Cybersecurity-Strategy-980x366.jpg
If you are searching about 4 Essential Steps to Cloud Computing Security • Messaging Architects you've visit to the right web. We have 35 Pictures about 4 Essential Steps to Cloud Computing Security • Messaging Architects like Cybersecurity And Cloud Computing Challenges | Skill Success, How Cyber Security Companies Overcome the Most Common Cloud Security and also Cisco extends SD-WAN options with AWS, Azure hybrid-cloud integration. Here it is:
4 Essential Steps To Cloud Computing Security • Messaging Architects
 messagingarchitects.com
messagingarchitects.com computing
Other Cloud Computing Security Challenges | Download Scientific Diagram
 www.researchgate.net
www.researchgate.net The Challenges Of Cloud Cybersecurity
 www.techsngadget.com
www.techsngadget.com 9 Ways To Boost Cloud Computing Cybersecurity
 www.avanteinsurance.com
www.avanteinsurance.com Top 4 Cloud Computing Security Challenges | Lucidchart Blog
 www.lucidchart.com
www.lucidchart.com security cloud challenges computing testing web incident diagram management lucidchart process resource tech center architecture organization
Cybersecurity Or Cloud Computing: What You Need To Know
 www.third-party-security.com
www.third-party-security.com Tutorial:Cloud Computing Security | Digital Marketing Agency | Web
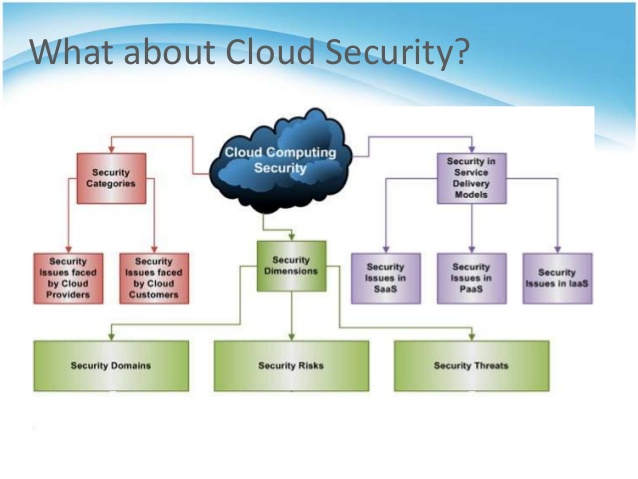 websitetoon.com
websitetoon.com Data Security Challenges In Cloud Computing - ZNetLive Blog - A Guide
 www.znetlive.com
www.znetlive.com cloud security data computing challenges 2021 znetlive wire19 environment major challenge field technology been information long
10 Best Cloud Computing Security Best Practices Today | Robots.net
 robots.net
robots.net Top 5 Cloud Computing Security Concerns - Driz Group
 www.drizgroup.com
www.drizgroup.com security computing cloud concerns medicaid provider
Cloud Security Challenges - DICC Blog
 dicc.in
dicc.in security cloud challenges dicc hacking ethical medium
THE DEBATE ON CLOUD COMPUTING VS CYBER SECURITY
 selfoy.com
selfoy.com Cloud Computing Security - Netsonic's Blog
 blog.netsonic.net
blog.netsonic.net cloud computing security
Benefits & Risks Of Cloud Computing And Cybersecurity
 l1n.com
l1n.com Cloud Computing Security Issues And Challenges | PhD Cloud Computing
 benisnous.com
benisnous.com cloud computing security challenges phd
Security Challenges Of Cloud Computing From Any Device.
 xcelcorp.com
xcelcorp.com How Cyber Security Companies Overcome The Most Common Cloud Security
 www.alliantcybersecurity.com
www.alliantcybersecurity.com challenges cybersecurity overcome common
Top Cloud Computing Security Challenges | Cybersecurity Automation
 www.cybersecurity-automation.com
www.cybersecurity-automation.com computing cybersecurity
Cloud Computing Security Challenges | Types Of Cloud Computing
 www.educba.com
www.educba.com computing security challenges
The Importance Of Cloud Computing In Your Cybersecurity Strategy
 cybersainik.com
cybersainik.com How To Conquer The Cybersecurity Challenges Of The Cloud? In 2020
 www.pinterest.com
www.pinterest.com prosyscom
Cloud Security Challenges
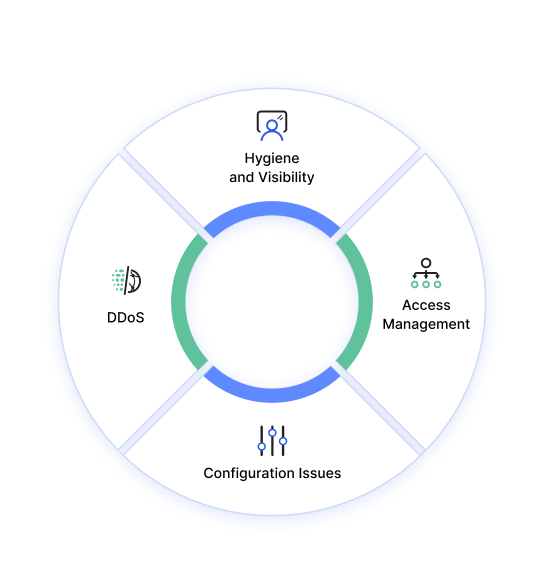 www.imperva.com
www.imperva.com imperva
Cloud Computing Security Issues And Challenges - Businesstechweekly.com
 www.businesstechweekly.com
www.businesstechweekly.com cloud security challenges computing issues
Conquering The Cyber Security Challenges Of The Cloud - CPO Magazine
 www.cpomagazine.com
www.cpomagazine.com conquering infrastructure hyperconverged cpomagazine
How Enterprises Can Combat Cybersecurity Challenges On The Cloud
 www.pinterest.com
www.pinterest.com hackercombat
How Cloud Computing Is Helping Cybersecurity - Guide [2019]
![How Cloud Computing is Helping Cybersecurity - Guide [2019]](https://www.computertechreviews.com/wp-content/uploads/2019/09/how-could-computing-is-helping-cybersecurity-Infographics.jpg) www.computertechreviews.com
www.computertechreviews.com computing helping cybersecurity cloud could guide security discuss detail
Everything You Need To Know About Cloud Computing Security
 www.fossguru.com
www.fossguru.com cloud computing security issues challenges everything need know source innovations quickly provided growing recent technology think lot threads people
Cloud Computing Security Issues And Challenges - Businesstechweekly.com
 www.businesstechweekly.com
www.businesstechweekly.com security challenges cloud issues computing these pitfalls overcome methods exploit organizations hackers common used
What Are Cybersecurity Risks Of Cloud Computing? - NJBIA
 njbia.org
njbia.org cybersecurity njbia
5 Advantages Of Cloud Computing Security Solutions | Cyberhunter
 cyberhunter.solutions
cyberhunter.solutions Cybersecurity And Cloud Computing Challenges | Skill Success
 www.skillsuccess.com
www.skillsuccess.com cloud cybersecurity challenges computing
What Is Cloud Computing And Cyber Security? | Cybersecurity Automation
 www.cybersecurity-automation.com
www.cybersecurity-automation.com cybersecurity
Cisco Extends SD-WAN Options With AWS, Azure Hybrid-cloud Integration
 soworos.blogspot.com
soworos.blogspot.com aws cisco computing wan metallic extends sase juniper
Secure Digital Cloud Computing Cyber Security Concept Stock
 www.dreamstime.com
www.dreamstime.com Challenges Of Cloud Computing
 thecustomizewindows.com
thecustomizewindows.com threats disadvantages mobility manitoba contribute provider cares
What are cybersecurity risks of cloud computing?. Cloud computing security issues challenges everything need know source innovations quickly provided growing recent technology think lot threads people. Cloud computing security issues and challenges
Post a Comment for "cloud computing and cyber security challenges Top 4 cloud computing security challenges"