Cloud computing has revolutionized the way businesses operate by providing seamless access to vast amounts of data and resources. However, with this convenience comes a whole new set of challenges, particularly in the realm of data security. As more and more organizations rely on cloud computing for storing and processing sensitive information, it becomes crucial to implement best practices to ensure the integrity and confidentiality of data.
Data Security Challenges in Cloud Computing

One of the main concerns in cloud computing is the risk of data breaches and unauthorized access. When data is stored in the cloud, it is essential to have robust security measures in place to protect sensitive information. Without proper security measures, data can be easily compromised, leading to severe consequences such as loss of customer trust, financial loss, and legal implications.
Another challenge in cloud computing is the issue of data privacy. Organizations must ensure that client data is adequately protected and that access to it is restricted only to authorized personnel. Data privacy regulations, such as the General Data Protection Regulation (GDPR), require organizations to implement stringent security measures to safeguard personal data.
Furthermore, data residency and compliance become critical considerations when adopting cloud computing. Organizations must have a clear understanding of the geographical location where their data is stored and whether it conforms to applicable laws and regulations. Some industries, such as healthcare and finance, have specific compliance requirements pertaining to data storage and processing.
Best Practices for Data Security in Cloud Computing

To mitigate the risks associated with data security in cloud computing, organizations should follow best practices:
- Implement Strong Authentication and Access Controls: Utilize multi-factor authentication and role-based access controls to ensure only authorized individuals can access data stored in the cloud.
- Encrypt Data: Use encryption techniques to safeguard data confidentiality both in transit and at rest. This ensures that even if data is intercepted or compromised, it remains unreadable without the decryption key.
- Regularly Update and Patch Systems: Keep cloud infrastructure and software up to date with the latest security patches to protect against known vulnerabilities.
- Perform Regular Security Audits: Conduct routine security audits to identify any vulnerabilities or weaknesses in the cloud infrastructure and promptly address them.
- Implement Data Loss Prevention Measures: Utilize data loss prevention tools and techniques to prevent accidental or intentional data leakage and unauthorized transfers.
- Train Employees: Educate employees on data security best practices, such as strong password management, identifying phishing attempts, and the responsible use of cloud resources.
- Monitor and Log Activity: Implement robust monitoring systems to track and log user activity in the cloud environment. This helps in detecting and responding to any suspicious or unauthorized behavior.
By adopting these best practices, organizations can enhance data security in cloud computing, minimize the risk of data breaches, and ensure compliance with relevant regulations. However, it is essential to continually assess and reassess data security practices as technology and threats evolve.
In conclusion, data security is a paramount concern in cloud computing. With the increasing reliance on cloud services, it is vital for organizations to implement robust security measures and adhere to best practices to protect sensitive data. By doing so, organizations can confidently leverage the benefits of cloud computing while safeguarding their valuable information from unauthorized access and potential breaches.
If you are searching about Cloud Security For Dummies - Benefits Of Cloud Computing you've came to the right page. We have 35 Pics about Cloud Security For Dummies - Benefits Of Cloud Computing like Data Security: An Integral Aspect of Cloud Computing | Cuelogic, Top 6 Cloud Computing Security Topics – F42 Community and also (PDF) Case Study of Cloud Computing Security and Emerging Security. Read more:
Cloud Security For Dummies - Benefits Of Cloud Computing
 www.cloudcodes.com
www.cloudcodes.com cloud security endpoint improve workload threats dummies organization tips computing safe february 2021
10 Best Cloud Computing Security Best Practices Today | Robots.net
 robots.net
robots.net Public Cloud Security Concerns Remain After Study
 www.tcdi.com
www.tcdi.com cloud security backup public should know skope things concerns remain study after digital
(PDF) Security Issues And Challenges In Cloud Computing
 www.researchgate.net
www.researchgate.net Cloud Computing Security Architecture Slideshare / Architecture Of
 veggieboxadventures.blogspot.com
veggieboxadventures.blogspot.com computing
What Is Cloud Computing Security? Definition, Risks, And Security Best
 www.spiceworks.com
www.spiceworks.com Addressing The Biggest Risks To Cloud Computing Security
 www.startexsoftware.com
www.startexsoftware.com cloud computing security risks addressing biggest saas risk management
Cloud Computing IT Security Standard | Templates At
 www.allbusinesstemplates.com
www.allbusinesstemplates.com computing allbusinesstemplates breach ict
(PDF) Case Study Of Cloud Computing Security And Emerging Security
 www.researchgate.net
www.researchgate.net Tutorial:Cloud Computing Security | Digital Marketing Agency | Web
 websitetoon.com
websitetoon.com Cloud Computing Security Vulnerabilities And What To Do
 ictframe.com
ictframe.com cloud computing precautions challenges vulnerabilities ictframe fossguru
Top 5 Cloud Computing Security Issues & Challenges | EC-Council
 www.eccouncil.org
www.eccouncil.org Data Center, Cloud Computing Security, And Storage Solutions | CTSBoston
 ctsboston.com
ctsboston.com security cloud computing data center
Data Security: An Integral Aspect Of Cloud Computing | Cuelogic
 www.cuelogic.com
www.cuelogic.com security cloud data computing aspect integral
Top 5 Cloud Computing Security Issues In 2021 | ImpactQA
 www.impactqa.com
www.impactqa.com impactqa
The Security Risks Of Cloud Computing - Tech America
 www.techamerica.org
www.techamerica.org Cloud Computing Security And Issues - TopThingz
 www.topthingz.com
www.topthingz.com cloud computing security issues topthingz data choose board
Why Does Cloud’s Oldest Concern — Security — Continue To Hang Around?
 www.forbes.com
www.forbes.com concern oldest around computing network
Cloud Computing Security Explained – WW Works
 wwworks.com
wwworks.com 8 Must-Have Cloud Computing Security Features Khabza Career Portal
 www.khabza.com
www.khabza.com computing backup khabza avepoint
Cloud Computing Security Risk Management | Virginia CPA Firm
 www.pbmares.com
www.pbmares.com computing
Why Invest In Data Security In Cloud Computing | IT Briefcase
 www.itbriefcase.net
www.itbriefcase.net cloud security computing data why investment good technology inquire owners starting days business these
Microsoft Azure Confidential Computing Ensures Improved Cloud Security
 www.itsupportsingapore.sg
www.itsupportsingapore.sg security cloud computing services azure microsoft ensures improved confidential khang ng wei comment leave
Top Cloud Computing Security Challenges | Cybersecurity Automation
 www.cybersecurity-automation.com
www.cybersecurity-automation.com computing cybersecurity
What Are The Security Risks Of Cloud Computing? | Expert Insights
 expertinsights.com
expertinsights.com risks computing
Data Security Challenges In Cloud Computing - ZNetLive Blog - A Guide
 www.znetlive.com
www.znetlive.com cloud security data computing challenges 2021 znetlive wire19 environment major challenge field technology been information long
Cloud Computing Security Issues And Challenges - Businesstechweekly.com
 www.businesstechweekly.com
www.businesstechweekly.com cloud security challenges computing issues
Cloud Computing Security Issues: What They Are And How To Face Them - Focus
 wearefocus.co.uk
wearefocus.co.uk cloud computing security issues face them they
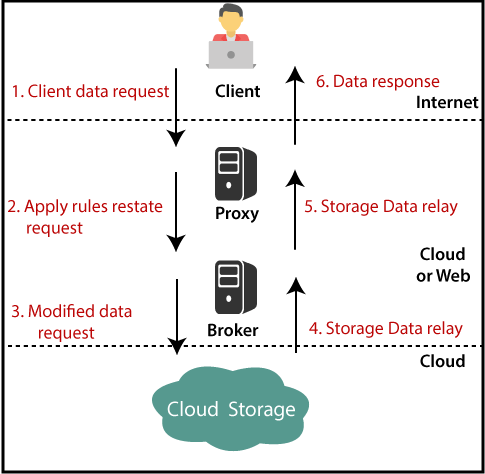
Cloud Computing Security
 www.tutorialandexample.com
www.tutorialandexample.com Advanced IT Cloud Security & Hacking Training Online Course
 gbhackers.com
gbhackers.com hacking training rapidly organizations higly evolving
Top 6 Cloud Computing Security Topics – F42 Community
 f42community.com
f42community.com ponder worry considerably organizations
Best Practices For Data Security In Cloud Computing | TurningCloud
 www.turningcloud.com
www.turningcloud.com maturing component rapidly enterprise
WatchGuard Takes Home 2020 Cloud Computing Security Excellence Award
 www.secplicity.org
www.secplicity.org cloud computing security sap watchguard migration award migrating rbk virtualisation dacast secplicity relentless pillars msp innovation capitalize mitigates disruptions unleashes
Ultimate Guide To Cloud Computing Security- Hire Cloud Expert | Chapter247
 www.chapter247.com
www.chapter247.com cloud security computing ultimate guide understand let detail
Top 4 Cloud Computing Security Challenges | Lucidchart Blog
 www.lucidchart.com
www.lucidchart.com security cloud challenges computing testing web incident diagram management lucidchart process resource tech center architecture organization
Top cloud computing security challenges. Security cloud challenges computing testing web incident diagram management lucidchart process resource tech center architecture organization. Data security: an integral aspect of cloud computing
Post a Comment for "cloud computing security articles (pdf) case study of cloud computing security and emerging security"