Cloud computing has become an integral part of our lives, offering convenience and flexibility like never before. However, with its many advantages, there are also certain security risks associated with it. In this post, we will explore some of the security risks of cloud computing and discuss effective measures to combat them, ensuring the safety of your data and sensitive information.
Security Risks of Cloud Computing

One of the primary concerns with cloud computing is the risk of data breaches. As we store our data and information on remote servers, there is always a chance that unauthorized individuals may gain access to it. This could potentially lead to a compromise of sensitive information, such as personal details, financial records, or intellectual property. It is crucial to address this risk proactively to prevent any security breaches.
Another significant security risk is the potential for data loss. While cloud service providers implement various redundancy measures to safeguard against data loss, there is still a chance that your data could become inaccessible or permanently deleted. This could occur due to hardware failures, natural disasters, or human errors. Implementing effective backup and recovery strategies is essential to mitigate the risk of data loss.
Combating Security Risks in the Cloud

To combat the security risks associated with cloud computing, it is crucial to adopt a multi-layered approach. Here are a few effective measures you can take to enhance the security of your cloud-based systems and data:
1. Strong Authentication and Access Controls
Implementing robust authentication mechanisms, such as two-factor authentication, can significantly reduce the risk of unauthorized access. Additionally, maintaining stringent access controls based on the principle of least privilege ensures that only authorized individuals can access sensitive data.
2. Data Encryption
Encrypting data before storing it in the cloud adds an extra layer of protection. This ensures that even if a breach occurs, the stolen data remains unreadable and unusable to unauthorized individuals. Implement encryption techniques both at rest and in transit for comprehensive data security.
3. Regular Security Audits and Updates
Frequent security audits and updates are vital to identifying and addressing any vulnerabilities in your cloud environment. By keeping your systems up to date and patching any known security vulnerabilities promptly, you can minimize the risk of exploitation by malicious actors.
4. Employee Awareness and Training
Investing in training programs to educate employees about the best practices in cloud security is crucial. By raising awareness about the potential risks and promoting a culture of security-consciousness, you can significantly reduce the likelihood of accidental data breaches caused by human error.

5. Regular Data Backups
Regularly backing up your data is one of the most effective strategies to combat the risk of data loss. Ensure that the backup copies are stored securely and regularly tested to verify their integrity. In the event of data loss, you can quickly recover your data and minimize any potential disruptions.
6. Choosing a Reliable Cloud Service Provider
Selecting a reputable and reliable cloud service provider is crucial for ensuring the security of your data. Conduct thorough research, read customer reviews, and evaluate the provider's security measures and certifications before making a decision. Working with a trusted provider significantly reduces the risk of security breaches.
By being aware of the security risks associated with cloud computing and implementing these proactive measures, you can safeguard your data and information effectively. Remember, proactive security measures are essential in this rapidly evolving digital landscape. Stay vigilant, stay updated, and protect yourself from potential security threats in the cloud.
If you are looking for Best Cloud Computing Risk Assessment Template PDF Example you've visit to the right place. We have 35 Pics about Best Cloud Computing Risk Assessment Template PDF Example like How Much Safe Your Personal Data/Files Are In Web Cloud Storage, Cloud Security: Understanding the Shared Responsibility Model Layots and also security risks associated with cloud computing | Cloud computing. Read more:
Best Cloud Computing Risk Assessment Template PDF Example
 kelitbanganwonogiri.org
kelitbanganwonogiri.org Security Risks Of Cloud Computing - CloudTerminology.com
 www.cloudterminology.com
www.cloudterminology.com risks
Cloud Computing Security And Risks Concerned In Cloud Computing Blog
 www.cloudhostworld.in
www.cloudhostworld.in cloud computing risks concerned security
Cloud Security: Understanding The Shared Responsibility Model Layots
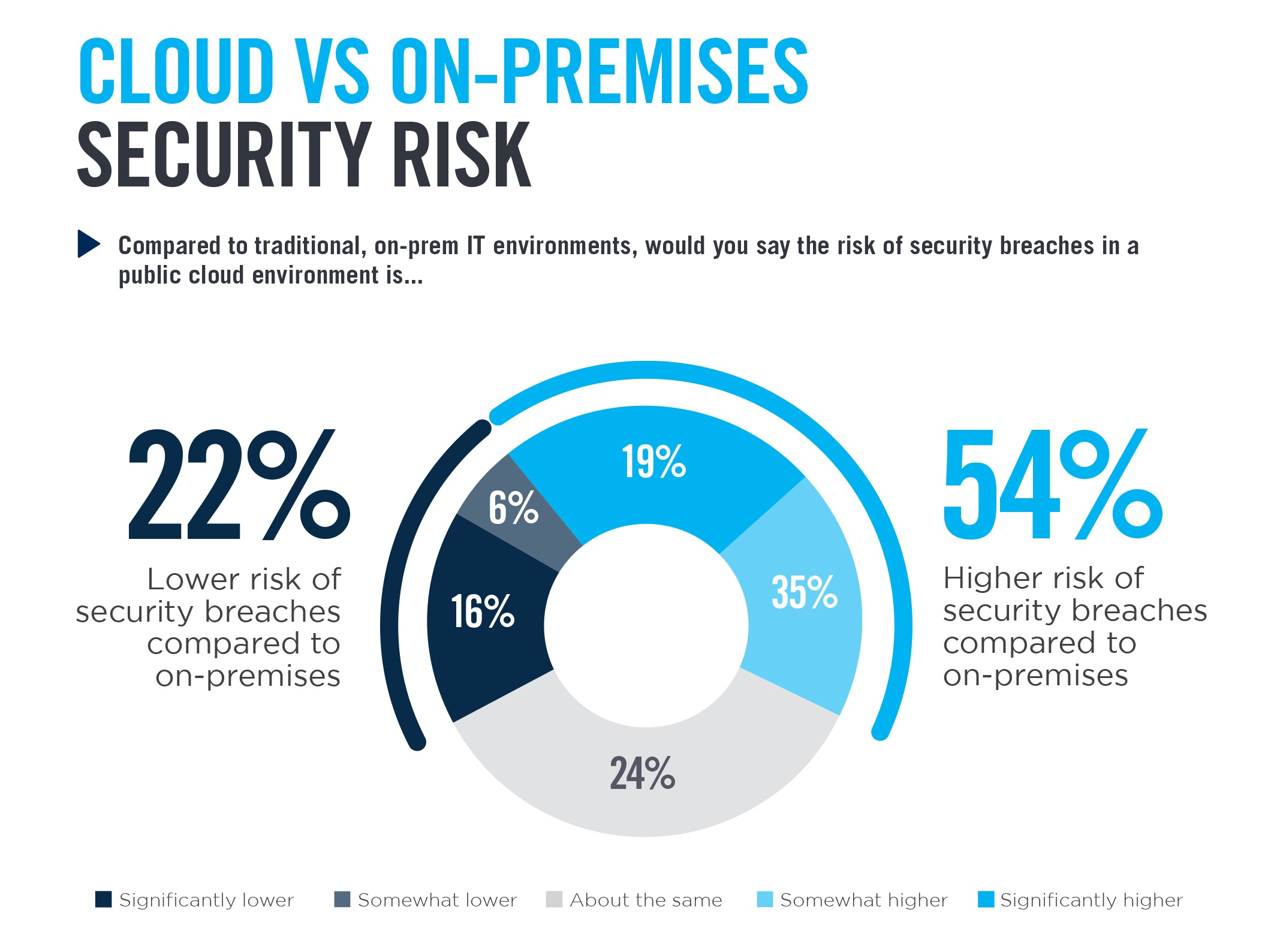 layots.com
layots.com devops layots risks neglect
Risks Of Cloud Computing Explained (Both Sides)
 www.slideshare.net
www.slideshare.net computing
What Are The Security Risks Of Cloud Computing - Codeavail
 www.codeavail.com
www.codeavail.com risks computing codeavail
Top 5 Risks Of Cloud Computing
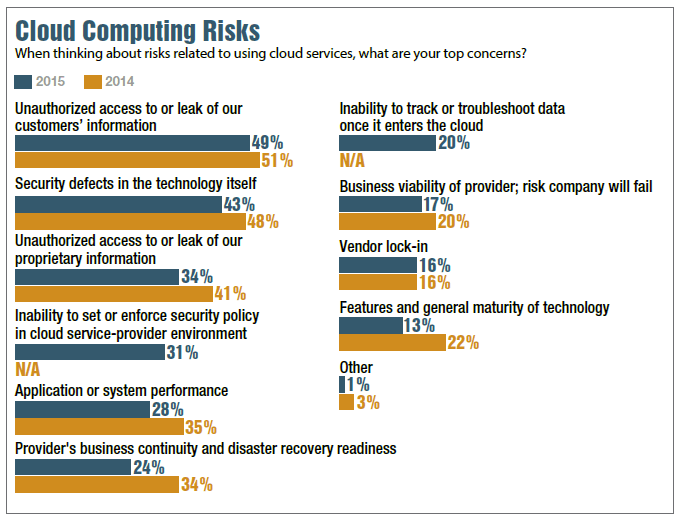 www.calyptix.com
www.calyptix.com cloud risks computing security identified threat
Eight Risks And Challenges For Cloud Computing – Skill Monk
 blog.skillmonks.com
blog.skillmonks.com computing challenges risks eight
Cloud Risk Protection | Proactive Cloud Security SecureSky
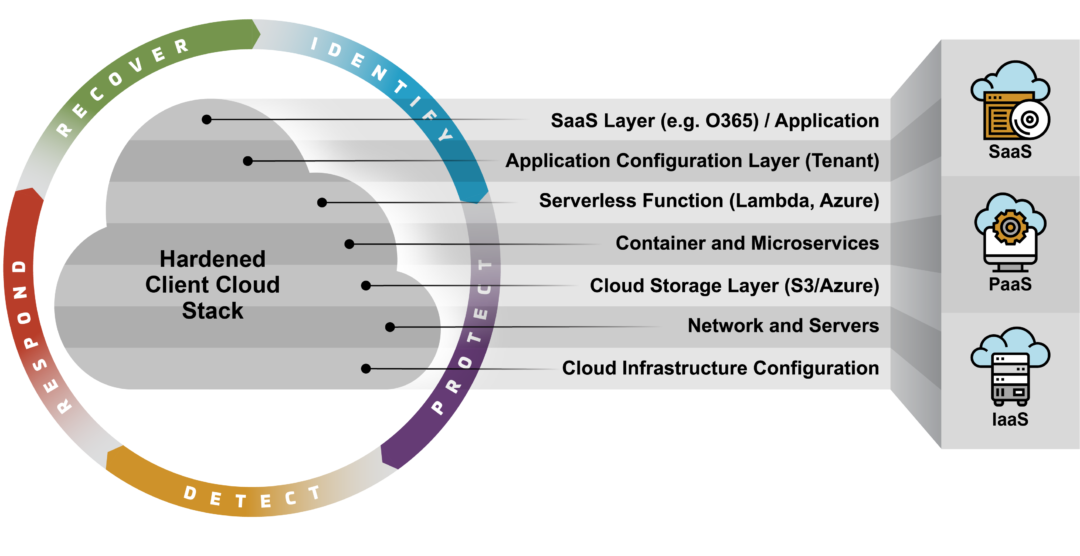 securesky.com
securesky.com security cloud threat assessment
Edge Computing Security Risks And How To Overcome Them - The
 www.thedissertationpapers.co.uk
www.thedissertationpapers.co.uk risks iot vulnerabilities overcome threats techtarget
Security Risks Of Cloud Computing And How To Combat Them
 www.getapp.com
www.getapp.com risks cloud security computing threats
Infographic - Cloud Security Concerns
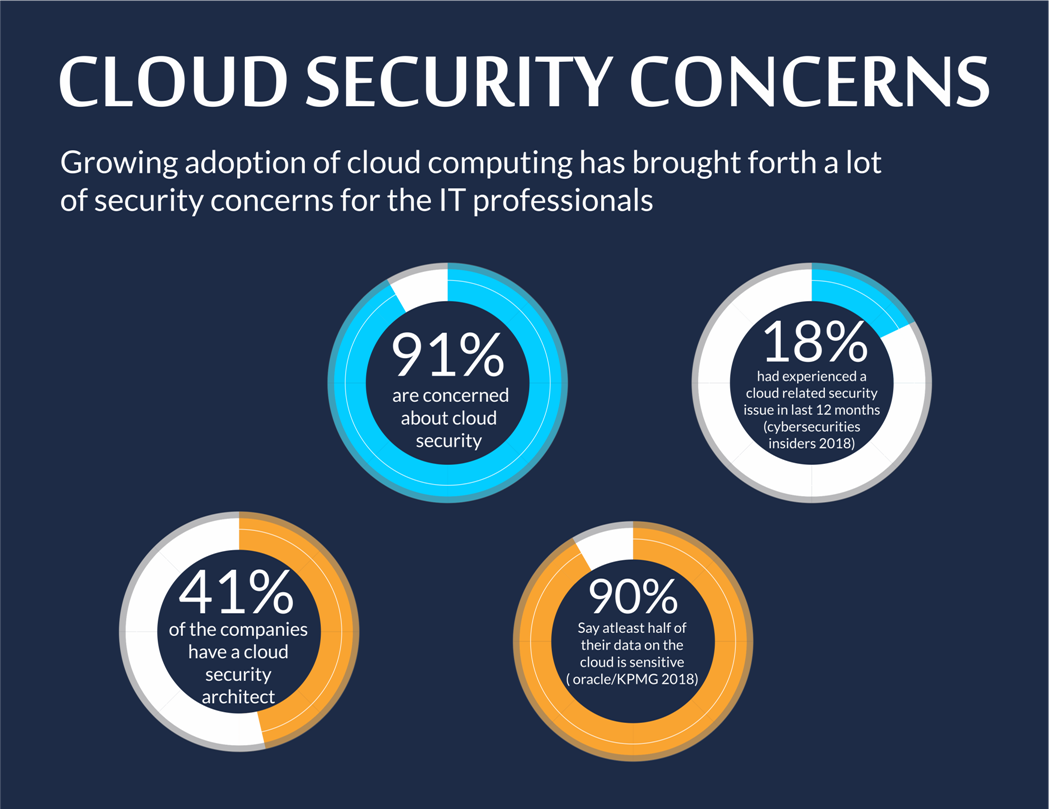 prasa-pl.com
prasa-pl.com security cloud concerns infographic
Security Risks For Cloud Computing - Cloud Security And Computing
 www.worthinlife.com
www.worthinlife.com What Are The Security Risks Of Cloud Computing? — Techslang
 www.techslang.com
www.techslang.com computing risks multicloud arnaque hui tant difficile viendra aujourd différents ashrafi heise
Fig. Cloud Computing Security Threats | Download Scientific Diagram
 www.researchgate.net
www.researchgate.net computing threats
What Is A Cloud Security Assessment? | CrowdStrike
 www.crowdstrike.com
www.crowdstrike.com cloud assessment security crowdstrike
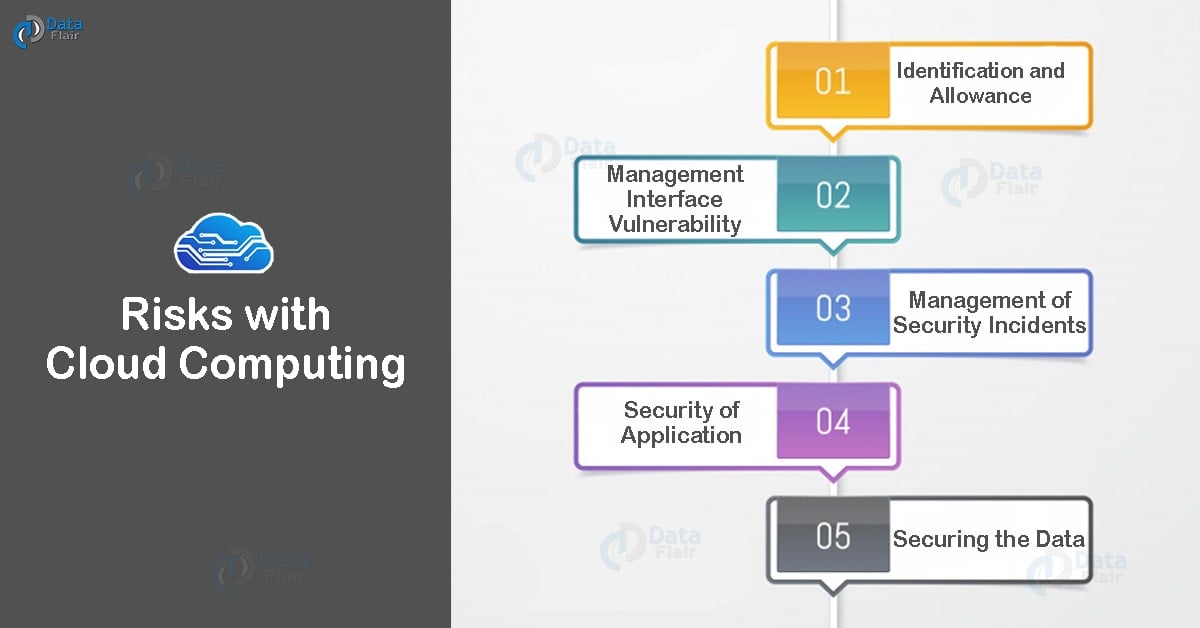
Cloud Security - Precautions & Risk Of Cloud Computing - DataFlair
 data-flair.training
data-flair.training risks precautions
Cloud Risk Assessment Identify Context
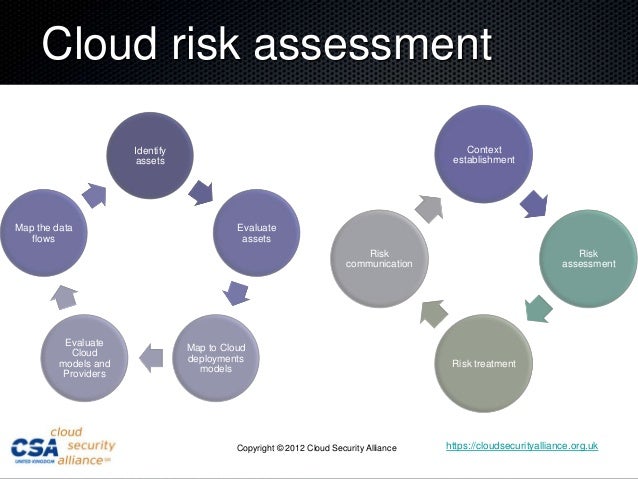 www.slideshare.net
www.slideshare.net cloud risk security assessment architecture slideshare identify context
Security Risks Associated With Cloud Computing | Cloud Computing
 www.pinterest.com
www.pinterest.com cloud security plan steps developing computing insight risks associated computer project process step board business choose training work
Do The Risks Of Cloud Computing Outweigh Benefits? | Risk Management
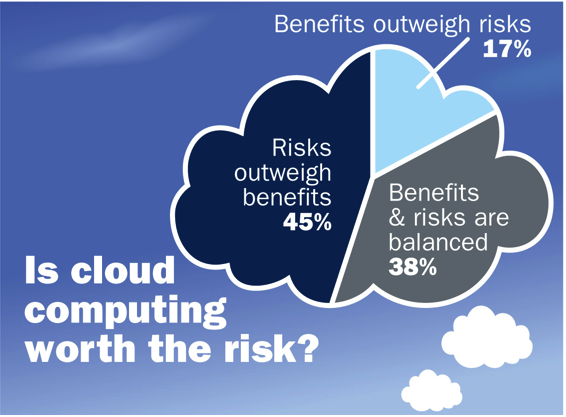 www.riskmanagementmonitor.com
www.riskmanagementmonitor.com cloud computing risks benefits risk outweigh
How Much Safe Your Personal Data/Files Are In Web Cloud Storage
 www.exeideas.com
www.exeideas.com cloud security risk storage risks data web exeideas network
Risks Of Cloud Computing | Top 4 Types Of Cloud Computing
 www.educba.com
www.educba.com cloud computing risks types science data tutorials tutorial
How To Protect Your Cloud: Guide To Cloud Security
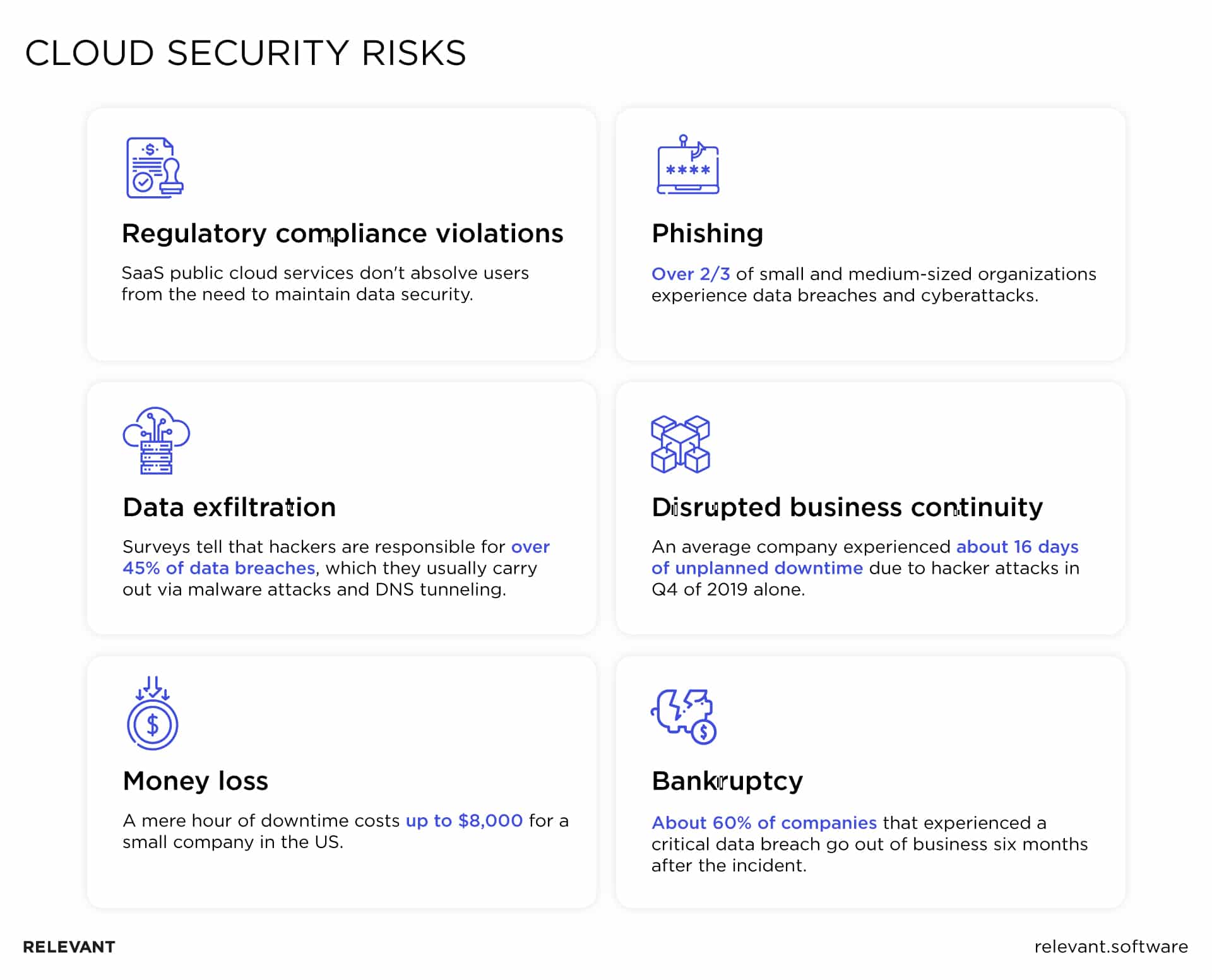 relevant.software
relevant.software risks protect due await implement dangers organizations
What Are The Security Risks Of Cloud Computing? - Kloudr
 www.kloudr.com
www.kloudr.com Cloud Infographic: Cloud Computing Risks And The Private Clouds | The
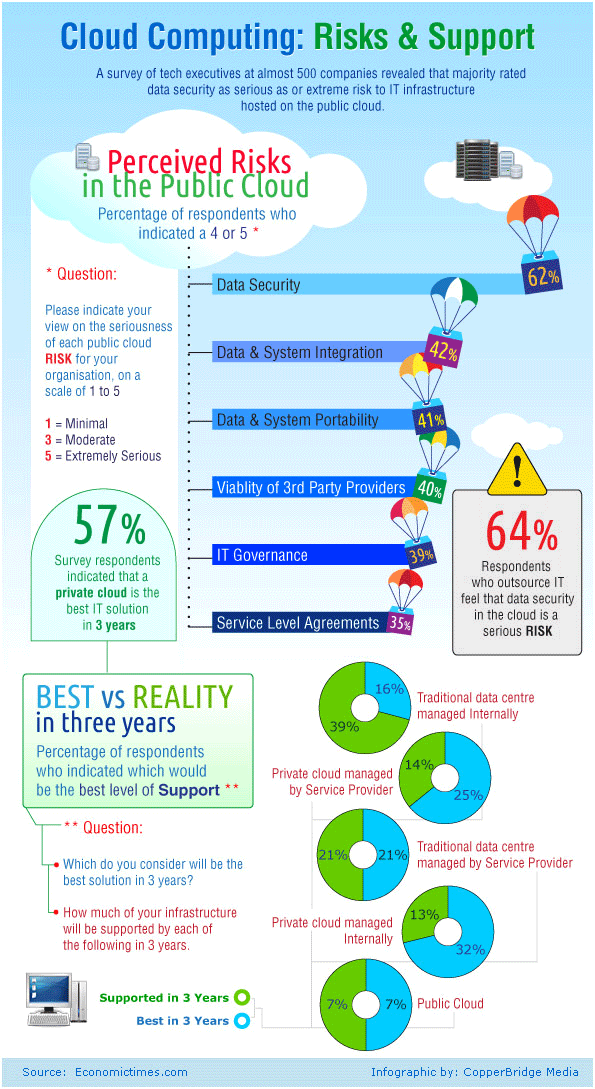 www.thecloudinfographic.com
www.thecloudinfographic.com cloud computing risks infographic clouds private risk
Managing The Impact Of Cloud Computing - The CPA Journal
 www.cpajournal.com
www.cpajournal.com cloud computing impact risk assessment roles responsibilities cpa managing management provider change document operations shared business analysis
The Major Risks Associated With Cloud Computing | British Assessment Bureau
 www.british-assessment.co.uk
www.british-assessment.co.uk computing cloud risks associated major assessment british
Cloud Computing Security Risks In 2020 & How To Avoid Them
 www.vervelogic.com
www.vervelogic.com cloud computing risks security vervelogic avoid them october
Becoming The Safe Choice For The Cloud By Addressing Cloud Fraud & Se…
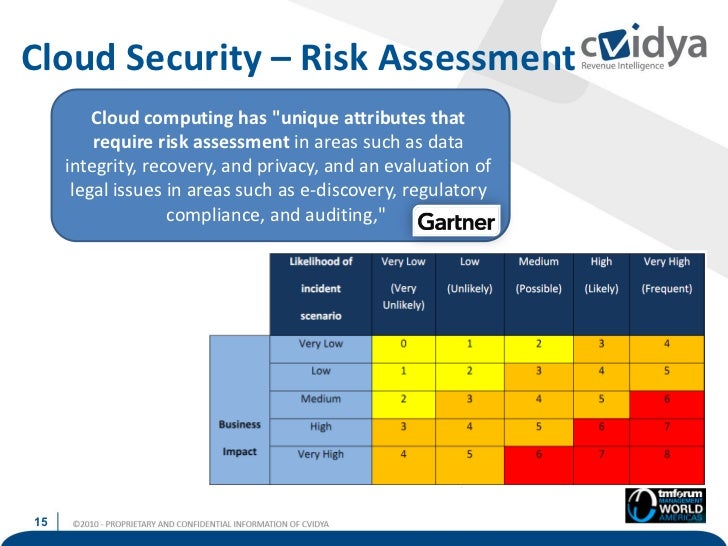 www.slideshare.net
www.slideshare.net cloud fraud addressing assessment threats computing
Patchy Clouds With A Chance Of Rain - Ask The IT Consultant
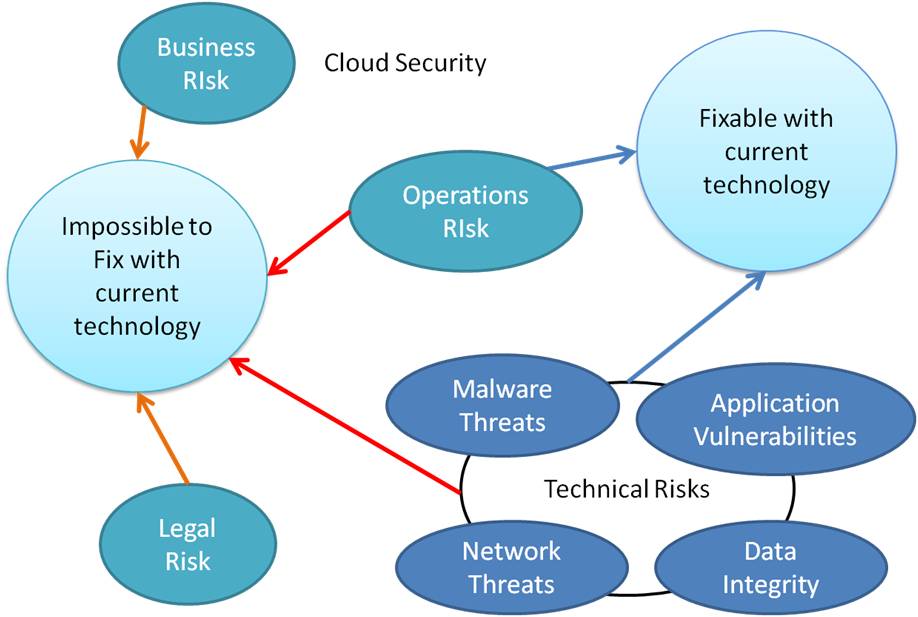 itknowledgeexchange.techtarget.com
itknowledgeexchange.techtarget.com security diagram cloud risks clouds figure patchy chance rain move
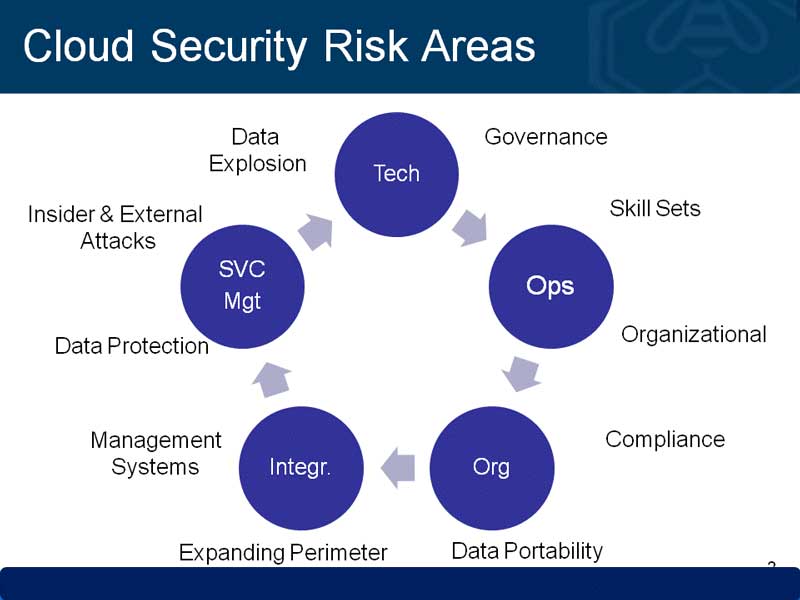
Classification Of Security Risks In Cloud Computing | Download
 www.researchgate.net
www.researchgate.net risks
Cloud Computing Risks. | Download Scientific Diagram
 www.researchgate.net
www.researchgate.net risks
How Structured Evals Allay Fears About Cloud Computing Security Risks
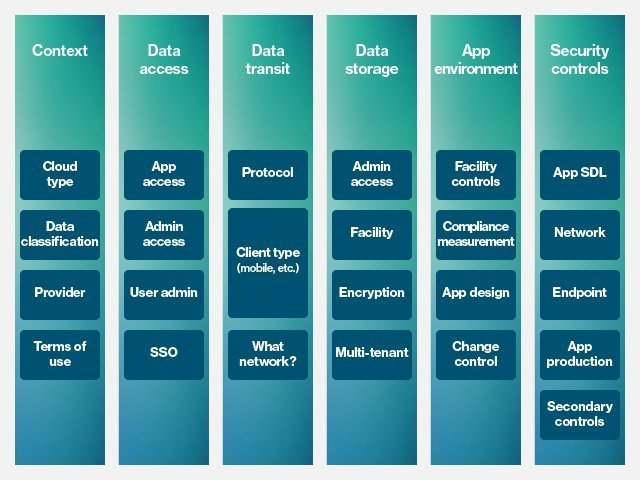 searchcloudapplications.techtarget.com
searchcloudapplications.techtarget.com cloud security assessment methodology risks evals computing fears allay structured framework podcast
Cloud Security - Risk Factors ~ The Technology Chronicle
 thetechnologychronicle.blogspot.com
thetechnologychronicle.blogspot.com scenarios
Cloud Computing Security Issues - Top 10 Cloud Security Concern In 2021
 www.cloudcodes.com
www.cloudcodes.com cloud security risks computing issues solutions challenges evaluating concerns regardless moving year
Cloud risk protection. Cloud infographic: cloud computing risks and the private clouds. Risks iot vulnerabilities overcome threats techtarget
Post a Comment for "cloud computing security risks and assessment What is a cloud security assessment?"